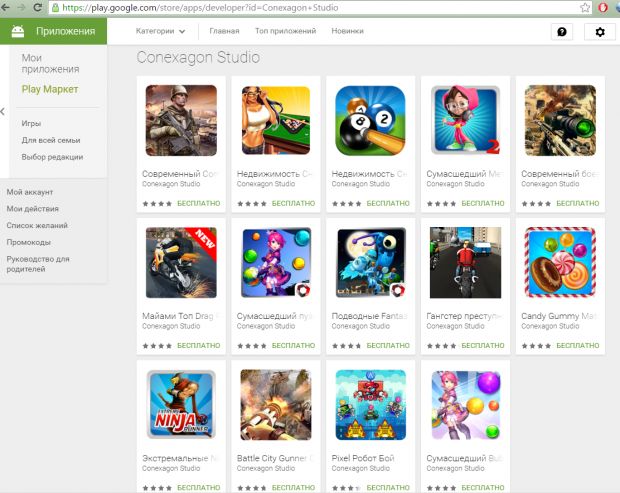
Security researchers discovered over 60 Android games on Google's official Play Store that were containing a malicious trojan named Android.Xiny.
These 60+ games were uploaded by 30 different developers, but they were all packed and behaving in the same way, as Dr.Web's security staff described.
Users who downloaded any of the games had their personal information collected and sent to a remote C&C (command and control) server.
Android.Xiny can show ads and download other malicious apps
The trojan gathered personal details such as IMEI and IMSI identifiers, country and language settings, mobile operator information, the phone's MAC address, OS version, what type of memory card the device was using, and from what app the trojan was collecting all this information.
The last bit of information makes sense collecting only when you have multiple malicious apps deployed, which might lead you to think that all the games might have been created and deployed by the same bad actor.
Once this data was sent to the C&C server, based on the victim's phone specifications, the malware operator would tell the trojan to display ads on the user's screen or escalate its presence on the device by downloading other malicious apps.
Android.Xiny does not gain root privileges, but it can download and launch other apps into execution, which in turn could contain code powerful enough to root the device and give the attacker more control over your phone.
Android.Xiny hid malicious downloads inside PNG images
A strange thing noted by Dr.Web's researchers for this campaign was the usage of steganography for downloading malicious apps. Steganography is the science of hiding data in plain sight, usually inside images.
Android.Xiny's operators chose to pack other Android apps inside a PNG image, instead of hiding its download via HTTPS traffic.
The reason behind this is that few security researchers performing reverse engineering would be suspicious of an image download, but would focus more of their efforts on observing and trying to track HTTPS traffic, a common avenue for delivering malware.
Currently, Dr.Web says that Google has failed to take down the apps it reported as infected with Android.Xiny.
 14 DAY TRIAL //
14 DAY TRIAL //