Google has paid $12,500 (€11,000) to security researcher Ramzes, for identifying an XSS (cross-site vulnerability) that could be used together with other exploits to send account recovery passwords to the attacker's email address, instead of the account's real owner.
According to a very complicated write-up, the attack is not easy to carry out and has already been fixed.
Researchers first found an XSS in a Google API
Google says the problem existed because of an XSS flaw in the API responsible for showing popups with information pulled from Google's Help Center. These popups are shown on various Google services like Docs, and their documentation pages.
As it turns out, Ramzes discovered that he could hijack the content of these popups, and use them as intermediary points to launch XSS attacks on other services. This was the first part of his bug report, for which he received $5,000 (€4,400).
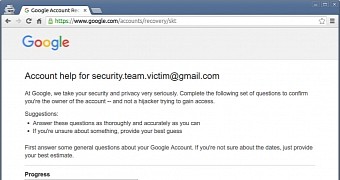
He then focused his efforts on the account recovery process. Since any user can start the recovery process for any Google email address, he began such a procedure for an email address he did not control (victim's email address).
Researcher found a way to pose as somebody else
Even if he knew he wouldn't be able to finish the process, by drawing an analogy between his own account's recovery process and the recovery of a victim's account, he was able to recover the anti-CSRF token for the victim's email account.
This token is used in private cookies, sent to users' browsers to validate their identities. With this token in hand, the researcher could now pose as the victim during a subsequent account recovery process.
The only thing he needed was some personal information which only account owners can supply, such as the date when the account was created, or the last time a victim successfully logged into his account.
An information leak to finish off the exploit
This information was displayed on Google's account migration page, seen when users want to move data between two different Google accounts.
Coincidentally, this page was also running on the same domain where the previous XSS bug was discovered, so the researcher managed to leak the needed information from Google's database.
Chaining all these flaws together, Ramzes demonstrated Google's staff how he could take over someone else's account.
Because he found such a unique way to chain all these exploits together, Google decided to award Ramzes an additional "Bug Chain Bonus" of $7,500 (€6,700).
This vulnerability was revealed on Google's recently launched blog, called "Best reports," where the company's security team plans to showcase some of the best bug reports it receives via its Vulnerability Reward Program (VRP).
 14 DAY TRIAL //
14 DAY TRIAL //