Tavis Ormandy, one of Google's most respected security researchers, has deferred a bug bounty reward to the Amnesty International organization after finding a security flaw in Bromium's micro-virtualization technology.
Bromium is a relatively new security vendor that has made a name for itself via its virtual hardware approach, and most specifically, via its endpoint solution called Bromium Enterprise Controller.
The company's software uses micro-virtualization (micro-VM) to protect against malicious code triggered into execution by user actions, such as clicking on links, opening email attachments, and interacting with files.
The Bromium challenge
Bromium was so sure of its product's ability to detect even unknown malware that it ran a competition at the recently concluded InfoSec Europe Conference, promising £10,000 ($15,000) to the first researcher who would manage to bypass its micro-VM system.
The company says that, in two days, researchers tried to infect a Bromium-protected PC to 189 strains of malware, ten of which were new creations. 1,500 malicious files and 4,800 websites later, the company was still in possession of the bug bounty reward after nobody managed to bypass the micro-VM system
On the closing day of the event, Google's Tavis Ormandy tweeted to the company claiming he found a host escape bug. In the subsequent conversations, the researcher revealed to Bromium's team not one, but two methods of bypassing their micro-VM technology.
Bromium engine bypass leads to RCE in Chrome and IE
The company now says it patched the flaws and will be paying the promised reward. Good guy Tavis deferred the reward's payment to Amnesty International, an international organization that campaigns to end grave abuses of human rights.
Bromium says it will wait a month, in order for its clients to update the Bromium engine, before releasing in-depth details about how the micro-VM bypass works.
Nevertheless, the company has released some clues about the bypass, explaining that Ormandy achieved remote code execution in the Chrome browser while accessing malicious links. The second bypass was similar to the first, but in Internet Explorer.
The company also added it would not offer a similar reward once again but is preparing to launch a dedicated bug bounty program.
"Tavis is one of the most respected ethical pen testers - and we hadn’t even given him our product," said Simon Crosby, Bromium CTO. "He willingly shared his findings and we spent a busy week validating them and discussing solutions with him. He was both gracious and helpful – and always impartial and data driven."
OK, found a quick @bromium host escape, I'll mail them right now. If they pay the £10,000 bounty, I'll donate it to Amnesty International. — Tavis Ormandy (@taviso) June 4, 2016
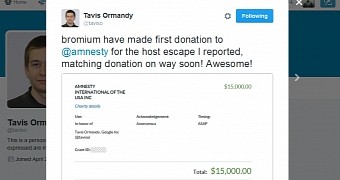
bromium have made first donation to @amnesty for the host escape I reported, matching donation on way soon! Awesome! pic.twitter.com/W6qU9azCDY — Tavis Ormandy (@taviso) June 20, 2016
 14 DAY TRIAL //
14 DAY TRIAL //