The latest update to Google Chrome Canary, the browser's unstable version that allows users to test experimental features, comes with an anti-tampering system meant to protect encrypted data transfers against attacks carried out by quantum computers.
For the past decade, companies like IBM, Intel, and Microsoft have been working hard on developing a fully functional quantum computer in order to be able to process larger amounts of data.
A quantum computer's power is measured in the ability to process qubits, or quantum bits, the homolog of bits on normal computers.
Quantum computers allow encryption attacks on archived Web traffic
While current implementations can handle only a handful of qubits, it is expected that, in the near future, these quantum computers will be able to achieve processing power large enough to carry out brute-force attacks against the encryption algorithms used to protect HTTPS and TLS traffic.
An attacker or state agency only needs to record and archive today's Web traffic, wait for a powerful enough quantum computer to be developed, and then use it to decrypt today's traffic.
Google's engineers said they understand the need to protect encrypted traffic across time, not only today. In order to protect today's data against tomorrow's attacks, the company is now including a project called New Hope into Chrome.
Chrome Canary features new hardened TLS key-exchange system
New Hope is a re-implementation of the Ring-LWE encrypted key-exchange protocol used with OpenSSL, specifically hardened to fend off quantum computing attacks. New Hope is included with Google Chrome version 54.0.2791.1, a.k.a. Canary SyzyASan.
"We explicitly do not wish to make our selected post-quantum algorithm a de-facto standard," writes Matt Braithwaite, Google Chrome Software Engineer. "To this end we plan to discontinue this experiment within two years, hopefully by replacing it with something better."
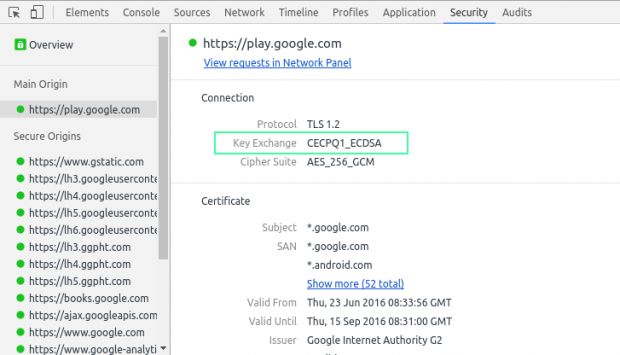
Until then, users can recognize if a website is using a quantum-computing hardened version of TLS by going to the Google Chrome Security Panel inside Developer Tools [press F12] and looking for the CECPQ1 label in the Key Exchange field, as pictured below.

 14 DAY TRIAL //
14 DAY TRIAL //