During the past seven days, two major companies, Dell and Google, have open-sourced two security-related tools for the purpose of helping system admins everywhere bolster up their local security measures.
The first one was Dell, who open-sourced a tool called DCEPT (Domain Controller Enticing Password Tripwire), which, in a simplified explanation, is a honeypot server for detecting attackers that might try and exploit local Windows domains and Active Directory setups.
DCEPT works by setting up a fake Windows domain and distributing so-called honeytokens to each client on the real network. It then starts listening in on any users trying to authenticate with one of the fake honeytokens. When this happens, based on the honeytoken, DCEPT can alert the system administrator about a compromised workstation.
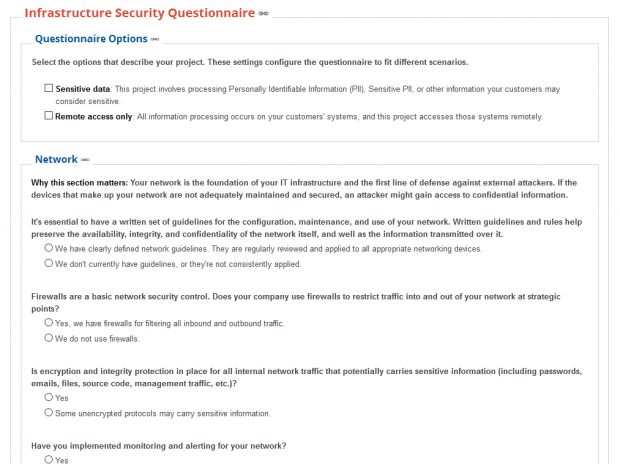
Google's tool is called VSAQ (Vendor Security Assessment Questionnaire) and is a "self-adapting questionnaires for evaluating multiple aspects of a vendor's security and privacy posture."
VSAQ is not necessarily a "tool," but more of a generic framework that contains a series of security questionnaire templates that system and network administrators can answer to get a general feel of the security measures their company has implemented so far.
Both tools, DCEPT and VSAQ, are available under open source licenses and can be downloaded via their GitHub repositories. Demos for some VSAQ questionnaires are also available online.

 14 DAY TRIAL //
14 DAY TRIAL //