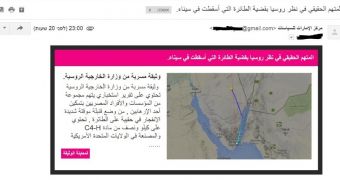
The Gaza Cybergang, also known as the Gaza Hackers Team, has developed a new malware strain named DustSky (or NeD Worm), which they've been spreading via phishing campaigns to targets in Israel, Egypt, Saudi Arabia, United Arab Emirates and Iraq, but also in the US and some European states.
Gaza Cybergang is an Arabic APT (Advanced Persistent Threat) cyber-espionage group that has been active since 2012. In the past, the group launched the DownExecute, XtremeRAT, and MoleRAT hacking campaigns.
According to ClearSky Cybersecurity, an Israeli company that has been keeping an eye on this threat, one of the group's members has developed new malware, specifically for infecting targets via email attachments and fake downloads.
The DustSky malware is distributed via spam email attachments
ClearSky security experts originally named the malware DustSky, but later they discovered that the hackers were referencing it internally with the NeD Worm name.
Researchers observed DustSky distributed via email attachments sent to a list of targets, but not via spear phishing campaigns. The difference is that all targets receive the same email, compared to spear phishing emails where each target gets a customized version of the email, based on their interests.
This tactic shows that the group has a select list of people it targets, but does not engage in deep target reconnaissance, nor does it send out blind spam to thousands of users, hoping to catch a government employee or foreign diplomat.
Besides spam email with politically charged subjects, the Gaza Cybergang has also launched classic phishing campaigns to fool targets into revealing their Yahoo, Google or Microsoft credentials, but the malware has not been used in these emails.
DustSky is also bundled with legitimate software targeting developers
Another method the group used to deploy the DustSky malware is through fake software downloads. This particular campaign was specifically aimed at software developers and tried to trick them into downloading malware-packed software updates for various legitimate applications (e.g. iMazing).
Links to these malicious websites serving DustSky-packed files have even been spotted on Freelancer.com, a well-known Web portal for developers looking for work.
As for its capabilities, the DustSky malware can extract passwords from popular browsers (via the BrowserPasswordDump utility packed with the malware), it can take screenshots of the user's desktop, get a list of active processes, and also search the computer for files containing specific keywords (e.g. resume, contacts, password, CV, etc.).
Additionally, the malware also contains a keylogger component and multiple features to avoid easy reverse engineering by security experts.
As with almost all modern-day malware, all the collected data is sent to a remote C&C (command and control) server, all via encrypted traffic to hide operations from snoopy security researchers.
Besides developers, ClearSky says it has also seen the malware deployed against government and diplomatic agencies. Additionally, people in the military defense, financial and mass media sectors have also been targeted.
DustSky technical details and infection steps are offered in ClearSky's DustSky report.
 14 DAY TRIAL //
14 DAY TRIAL //