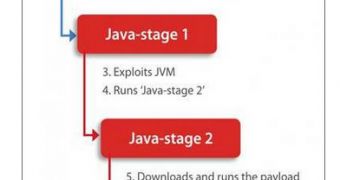
Trusteer experts have come across an interesting variant of the Java exploit kit called “g01pack.” g01pack is different from other exploit kits because it delivers its payload via a multistage attack.
“The first stage of the attack, the exploit shellcode, executes a second stage, in which a Java class runs in a separate Java process. This second Java process then downloads and runs the final payload,” Trusteer’s CTO Amit Klein wrote in a blog post.
According to Klein, this might be the first exploit kit that uses such a technique to deliver its payload.
So what are the benefits of such a multistage attack?
Experts say that by adding a “mid-course” stage to the exploit kit, it’s more likely that the attack will bypass security products.
In the tests performed by Trusteer, only 8 out of 46 tools detected the first stage JAR file as being malicious. The second stage class file was flagged by only two of the tools.
One attack observed by the security firm leveraged the CVE-2012-1723 Java sandbox bypass vulnerability to deliver the payload. Despite the fact that this security hole was fixed almost one year ago, there are still enough computers that run unpatched versions of Java.
The implementation details of this Java exploit are similar to the ones used in the BlackHole exploit kit, but BlackHole doesn’t use this multistage approach.
The g01pack exploit kit is used to distribute various malware families, including ZeuS, Gozi, Shylock and Torpig.
The crimekit is currently utilized to infect computers from all over the world. The infection rate is estimated at 1:3,000 devices per month, which means that the multistage approach is highly effective.
“‘g01pack’ is among the most successful exploit kits available today. It executes a ‘drive-by download’ attack that results in the silent installation of malware. Using the multi-staged attack the ‘g01pack’ exploit kit can effectively distribute advanced malware evading detection by existing security controls,” Klein noted.
Additional technical details on how the exploit kit works are available on Trusteer’s blog.
 14 DAY TRIAL //
14 DAY TRIAL //