Security researcher Michael Gillespie has created a decrypter that can help victims of the Unlock92 ransomware recover their files for free.
Unlock92 is a new ransomware variant first spotted by Malwarebytes security researcher S!Ri yesterday. The ransomware is actually from the same author of the Kozy.Jozy ransomware that appeared over a week ago.
Unlock92 ransomware is related to Kozy.Jozy ransomware
While Kozy.Jozy used a strong RSA-2048 algorithm system that prevented researchers from cracking its encryption routine, it appears that its author decided to make some modifications to Unlock92's codebase that eventually weakened its defenses.
Users can visit the ID Ransomware service to detect with what type of ransomware they are infected, but they can easily spot a Unlock92 infection based on the CRRRT extension it adds to each encrypted file.
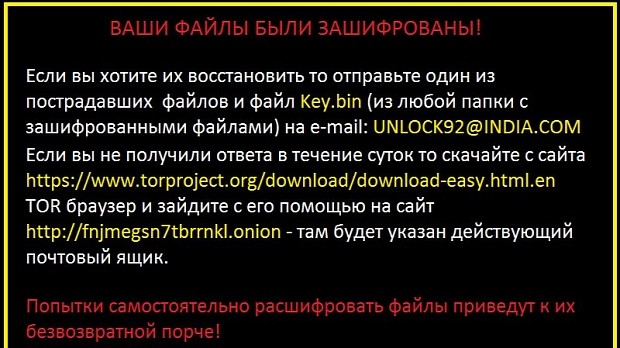
Additionally, the ransomware also changes your wallpaper with a message that tells you to send an email to [email protected].
Unlock92 uses a 64-character hexadecimal password to lock files
When locking files, Unlock92 generates a random 64-character hexadecimal password for each infected user. Files are encrypted with a symmetric AES encryption, and the above password is encrypted with RSA and sent to the criminal's server. The ransomware targets the following file extensions:
.cd, .ldf, .mdf, .max, .dbf, .epf, .1cd, .md, .db, .pdf, .ppt, .xls, .doc, .arj, .tar, .7z, .rar, .zip, .tif, .jpg, .ai, .bmp, .png, .cdr, .psd, .jpeg, .docx, .xlsx, .pptx, .accdb, .mdb, .rtf, .odt, .ods, .odb, .odg
Additionally, in spite of the fact the presence of a ransom note in Russian, the ransomware doesn't use any type of geo filters, as Michael Gillespie told Softpedia, and will encrypt the computer of any user, regardless of his country of origin or system language.
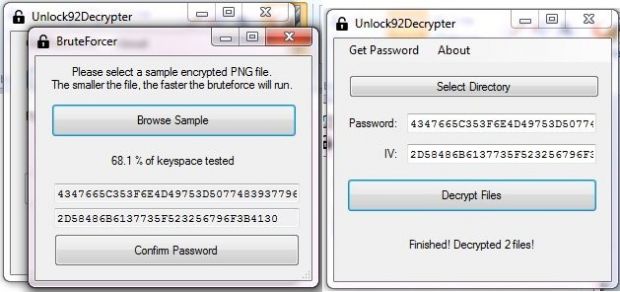
Michael Gillespie's Unlock92 decrypter is available for download from here. Here are his instructions for using it:
“ To generate the key and IV, you will need an encrypted PNG file (*.png.CRRRT); the smaller the file, the better. This may take some time, but shouldn't be more than an hour for a small file on most machines - my i7 can tear through a 1KB file and find the key in a few minutes. Simply load it into the brute-forcer, and let it go. Once it finds a key, click 'Confirm Password,' then select a folder to decrypt. ”
Just to be safe, the best option is to make a backup of your encrypted files first, just in case something horrible happens during the decryption process and messes up your files.Even if Unlock92 is from the same author, victims infected with Kozy.Jozy can't recover their files with this decrypter.
 14 DAY TRIAL //
14 DAY TRIAL //