It didn't take long for the crooks behind the Neutrino Exploit Kit (EK) to update their automated malware infection technology with exploit code foolishly open-sourced by a security startup on GitHub.
Back in May, Microsoft announced it patched a vulnerability (CVE-2016-0189) in the Internet Explorer scripting engine that was affecting Internet Explorer 9, 10 and 11, as well as Internet Explorer 11 running on Windows 10.
Symantec discovered that this particular exploit was used in targeted attacks against South Korean organizations.
CVE-2016-0189 exploit code finds its way to GitHub
In mid-June, security researchers from Theori compared the original and patched programs to identify what Microsoft had fixed and where the vulnerability had been.
This is nothing out of the ordinary since most companies provide technical analysis of security flaws so that other infosec experts can learn about the bugs and create defensive measures such as firewalls and antivirus products that can detect the exploitation of those vulnerabilities.
What Theori did was to take it one step further and craft a fully working weaponized exploit and then publish it on GitHub.
The authors of the Neutrino EK, the largest exploit kit on the market after the disappearances of Angler and Nuclear, only had to copy-paste the code and add it to their regular exploit chain.
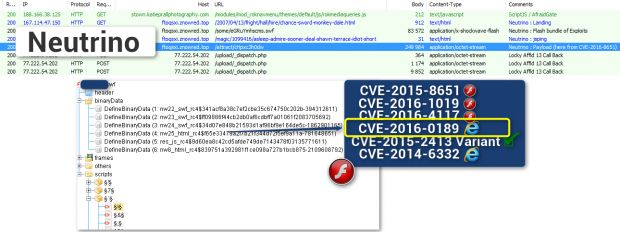
Multiple sources confirm Neutrino's new CVE-2016-0189 exploit
Independent security researcher Kaffeine, along with security vendors Qihoo 360 and FireEye, was quick to spot the new exploit in Neutrino live installations.
FireEye says that, at the moment, the open-source exploit only includes weaponized code that targets and infects IE users on Windows 10. Nevertheless, "[i]t is possible that attackers could use or repurpose the attack for earlier versions of Windows," the FireEye team notes.
As for attribution, FireEye says the exploit embedded within Neutrino is identical to the GitHub exploit, except for a small part at the beginning, most certainly modified by Neutrino authors to fit the code in their own exploit chain.
Another case of why malware code should never be open-sourced and left on public code repositories like GitHub is that of the my-Little-Ransomware project that was later used to create the cuteRansomware family.

 14 DAY TRIAL //
14 DAY TRIAL //