A piece of Android-based mobile ransomware has made the jump and is now capable of infecting and locking smart TVs running on the Android OS, security researchers are reporting.
Called FLocker (Frantic Locker), this ransomware appeared in May 2015, and Trend Micro says it detected over 7,000 different versions as its code kept evolving.
Only in April 2016, Trend Micro says it identified over 1,200 FLocker variants, as there was a visible development push behind this threat.
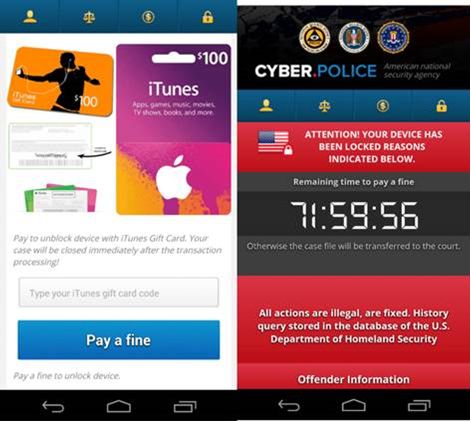
Trend Micro has not confirmed this, but the ransom screen seems to be identical to the ones used by the Cyber.Police (Dogspectus) ransomware. Back in April, around the same time of the spike in FLocker development, Blue Coat and Zimperium reported that Cyber.Police gained the ability to infect Android devices without any user interaction.
FLocker lies in hiding for 30 minutes
For this most recent evolution in FLocker's capabilities, Trend Micro explains that crooks are spreading the threat via SMS spam that contains malicious links.
Once users download the malicious apps spread through these links, the malware lies in hiding for 30 minutes. To avoid antivirus analysis, the malicious code is hidden in an HTML file inside the raw data "Assets" folder. This file conceals a DEX file with malicious routines.
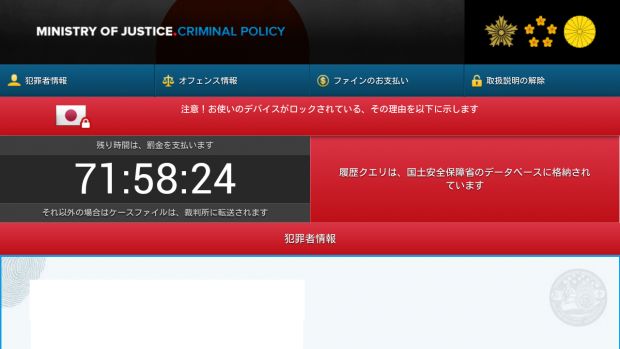
After the 30-minute timer runs out, Flocker starts pestering the user to give it admin rights. If the user declines, FLocker freezes the screen with a fake system update message to scare them into giving it the required access.
After FLocker gains administrator privileges, it will start talking with its C&C server, from where it downloads another APK and the ransom note in the form of an HTML&JS file.
FLocker only recently gained the ability to target smart TVs
FLocker shows the ransom note on the entire screen and starts the second APK, which encrypts files with a hardcoded AES encryption key.
While previously FLocker worked only on mobile devices, recent versions have started encrypting data on smart TVs running on the Android OS as well.
The Android OS versions running on mobile devices and smart TVs are different, so not necessarily all Android malware will run on both. It's obvious that crooks added this behavior intentionally.
FLocker avoids Eastern European countries
FLocker asks users for $200 in iTunes gift cards and will avoid running on devices located in the following countries: Kazakhstan, Azerbaijan, Bulgaria, Georgia, Hungary, Ukraine, Russia, Armenia, and Belarus.
Symantec researchers predicted the rise of smart TV ransomware last year. Trend Micro researchers recommend the following to all users infected with FLocker on their smart TV:
“ If an Android TV gets infected, we suggest user to contact the device vendor for solution at first. Another way of removing the malware is possible if the user can enable ADB debugging. Users can connect their device with a PC and launch the ADB shell and execute the command “PM clear %pkg%”. This kills the ransomware process and unlocks the screen. Users can then deactivate the device admin privilege granted to the application and uninstall the app. ”
FLocker should not be confused with the old trojan of the same name that targeted mobiles running the Symbian OS back in 2009.
 14 DAY TRIAL //
14 DAY TRIAL //