Vulnerabilities known as IODR (Insecure Direct Object References) were found and fixed in Worldpay, an online secure payments platform, security researcher Randy Westergren reports.
An IODR vulnerability is when users have access to information they should not see, either because it belongs to another user or originates from an account with higher privileges.
In 2013, the OWASP project classified IODR flaws as the fourth most prevalent and dangerous vulnerabilities around, mainly because they're incredibly easy to exploit and often expose a trove of information at once.
Access to transactions details
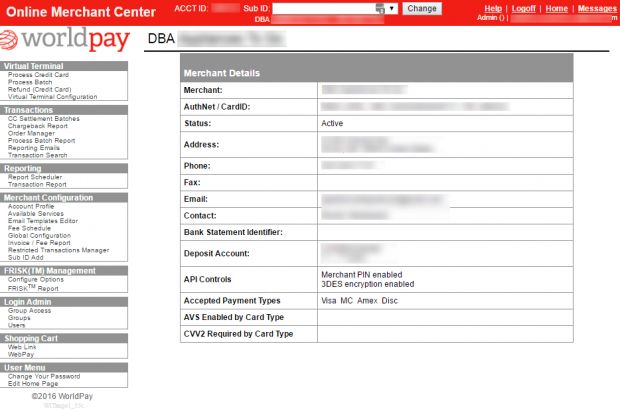
According to Westergren, such flaws affected Worldpay's merchant portal (Worldpay Online Merchant Center), an application where store owners can set up payment solutions for their businesses.
As with any payments portal, Worldpay solution also allowed store owners to view in-depth details about past payments. The researcher discovered that the HTTP request that loaded these details allowed an attacker to modify certain parameters and view the payment details for any other Worldpay transaction.
This included very sensitive details about the users involved in the transaction, but to Worldpay's credit, the full credit card number wasn't included, but only the last four digits. Unfortunately, there are many scammers who can find even this information useful.
Access to Web payment forms
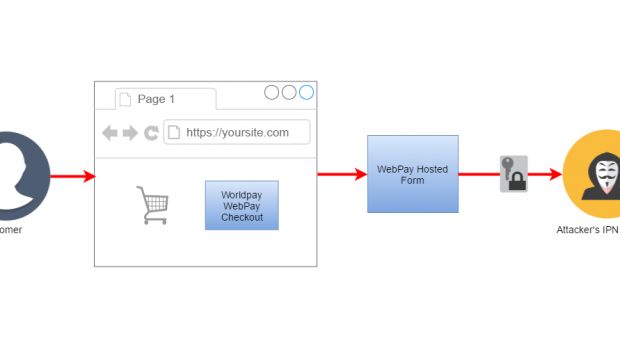
The second IODR issue he discovered was located in the form builder application that lets store owners create custom payment forms to add to their sites.
As before, Westergren realized that, by tweaking around with the HTTP request that loaded this form, he could fool Worldpay's servers into providing him access to other forms or even saving information inside them.
The attack scenario for this issue is simple, with a malicious actor adding rogue JavaScript code to any store's form, which he could use to log and steal payment information.
Both issues were fixed, but the researcher remained somewhat unsatisfied with Worldpay, mainly because they were still using an antiquated server infrastructure, running their merchant portal on IIS6, a technology that Microsoft officially deprecated in July 2015.
"The larger question remains: how are these vulnerabilities being introduced (and not identified/patched) into a company’s software, whose entire business is working with some of the most sensitive user data in existence?" the researcher noted on his blog.
 14 DAY TRIAL //
14 DAY TRIAL //