A series of bugs discovered in Kerio Control firewalls allow external attackers to hack into a company's internal network just by tricking employees into accessing a malicious link.
SEC Consult, a company that provides security consultancy services, has discovered the flaws in Kerio Control, a high-tech full security system that provides a network firewall, router, intrusion detection and prevention (IPS), gateway anti-virus, VPN, and web content and application filtering, all in one product.
SEC Consult says it discovered a slew of security vulnerabilities and two methods of combining them to gain access to the firewall and the networks behind it.
Brute-forcing the Kerio admin via an employee's computer
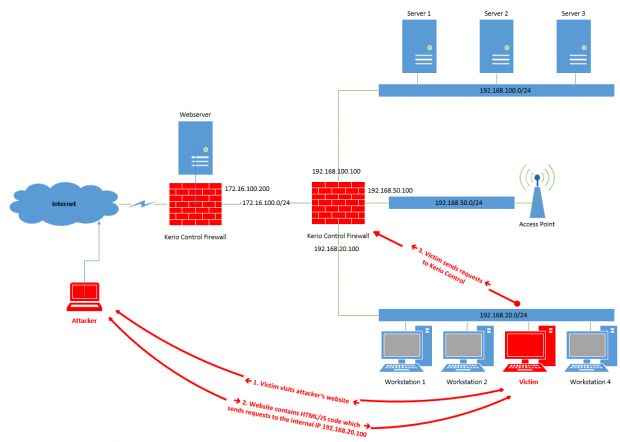
The first method is probably the easiest to exploit and relies on tricking a company employee into accessing a malicious page. This page uses images, forms, and JavaScript code to launch an attack, leveraging the user's PC as a pivot point inside the company's internal network.
Behind the scene, the attacking page uses a script to determine the user's internal IP address and then tries to load an image on the user's page that is hosted by the Kerio Control firewall. It tries this by attempting to load it via various internal IPs, based on the user's determined internal IP address. When the image loads, JavaScript on the page detects it and passes the firewall's IP address to another attack module.
This module, in turn, will brute-force the Kerio Control firewall backend panel for the admin credentials.
The attacker, also via the victim's computer, then uses other exploits to upload a reverse root shell on the firewall, which grants him access from anywhere in the world. A video explanation for this attack is embedded at the end of this article.
Upgrading the firewall with a reverse shell
The second exploitation chain is even simpler to carry out. Back in 2015, a SEC employee discovered two issues affecting the firewall's upgrade functionality.
The employee's exploitation chain involved a remote code execution (RCE) flaw and a cross-site scripting (XSS) issue.
When he told Kerio's staff about it, they only fixed the XSS flaw but left the RCE unpatched. The researcher only had to find another XSS issue to revive his attack.
Two issues still linger
In total, SEC Consult staff found 9 issues: 1) Unsafe usage of the PHP unserialize function and outdated PHP version leads to RCE 2) PHP script allows heap spraying 3) CSRF Protection Bypass 4) Web server running with root privileges 5) Reflected Cross Site Scripting (XSS) 6) Missing memory corruption protections 7) Information Disclosure leads to ASLR bypass 8) Remote Code Execution as administrator 9) Login not protected against brute-force attacks
Kerio patched all reported issues with the release of Kerio Control version 9.1.3, except for two (4 and 8). The company's response to SEC Consult for these issues was "I [We] do not consider this a vulnerability."
Furthermore, after Kerio released a patched version of their product, SEC Consult researchers found yet another XSS issue which re-activates the second exploitation chain.

 14 DAY TRIAL //
14 DAY TRIAL //