Fitness trackers produced by FitBit can "theoretically" be used to spread malware and can be infected in less than 10 seconds, claims Axelle Apvrille, a security researcher for FortiNet.
According to Axelle's findings, the reported vulnerability is quite easy to exploit, and the only condition is for the attacker to be close enough to their victim so that a Bluetooth connection can be achieved between the wearable and the hacker's laptop.
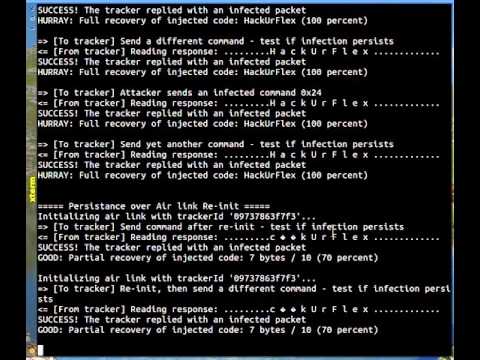
Infection usually takes up to 10 seconds while an infected network packet is sent to the FitBit device, and once achieved, the infection is boot-persistent, which means that restarting it does not clean the fitness tracker, a method that works for routers and other IoT devices.
From this point on, the FitBit tracker acts like a malware-spreading agent, infecting with its malware any other device it connects to.
The FitBit fitness tracker can spread any type of malware
As the security expert explains, both regular PCs and other FitBit trackers can be infected at the same time, and the attacker can use the fitness tracker to spread trojans, ransomware, adware, or anything else they desire.
Axelle discovered the vulnerabilities back in March and reported them to FitBit as a proof-of-concept finding. The fitness tracking company apparently decided not to fix the issues, telling The Register that the reason was that they were not used in real-life attacks and did not pose any threats to its users.
Previous to this, FitBit was in the news for two other security incidents. In 2013, hackers were able to access FitBit user accounts due to a weak authentication system, while in 2011, user data that detailed sexual activities was exposed online and was accessible via search engines.
Mrs. Apvrille is scheduled to present her findings today at the Hack.Lu conference in Luxembourg. A proof-of-concept video can be viewed below.
 14 DAY TRIAL //
14 DAY TRIAL //