A POS (Point of Sale) malware family has just taken a dangerous turn in its evolution after Trend Micro researchers observed that it has now gained the ability to replicate itself and spread to other local systems.
Called FighterPOS, this malware family was first seen in April 2015, when Trend Micro researchers discovered it targeting POS terminals in Brazil.
At that time, researchers speculated that FighterPOS was a one-man operation, probably run by a local Brazilian hacker. Trend Micro also reported that the person behind the malware used it to steal 22,000 credit card details and that its author was selling a version of his malware on the Dark Web for around $5,000 (€4,500).
FighterPOS evolves into Floki Intruder
Based on data picked up by their security products, the same Trend Micro experts are now reporting on a new variation of the FighterPOS malware family, which they dubbed Floki Intruder.
According to their investigation, this variant is not developed by the same person that created the original FighterPOS malware. It appears that the source code was sold to someone else, or that the hacker behind the first version might have joined forces with someone else.
File compilation details reveal that a different person put together Floki Invader, a theory that's also reinforced by the fact that many source code functions and comments are now in English, not Portuguese as they were in FighterPOS.
Floki Intruder can replicate itself
Floki Intruder appears to be much dangerous than the old FighterPOS version. The main difference is the presence of a worm-like feature that goes into effect after Floki infects computers.
This worm-like feature will scan the local network for similar POS terminals, clone itself and infect those devices as well.
"Adding this routine, in a way, makes sense: given that it is quite common for PoS terminals to be connected in one network," Trend Micro's Erika Mendoza and Jay Yaneza explain. "A propagation routine will not only enable the attacker to infect as many terminals as possible with the least amount of effort, it will also make this threat more difficult to remove because reinfection will occur as long as at least one terminal is affected."
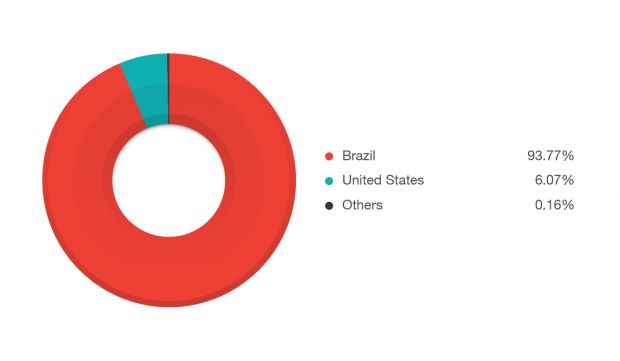
Despite the presence of English code in the malware's source, FighterPOS (Floki Intruder) has not moved outside Brazil. Over 93% of all FighterPOS infections are coming from Brazil while only 6% of infected terminals are located in the US.

 14 DAY TRIAL //
14 DAY TRIAL //