Ransomware often tries to disguise its malicious behavior using various tricks. The latest method observed is that employed by a new variant called Fantom, which shows a fake Windows Update screen while, in reality, it's encrypting the user's files.
The ransomware, spotted for the first time only a few days ago by AVG security researcher Jakub Kroustek, is coded on top of EDA2, a ransomware building kit that was open-sourced last year but eventually taken down.
EDA2 contained flaws that allowed researchers to obtain the decryption keys from the ransomware's C&C server. According to an analysis from Bleeping Computer, those flaws aren't there anymore, meaning one of the Fantom coders must have found and fixed them.
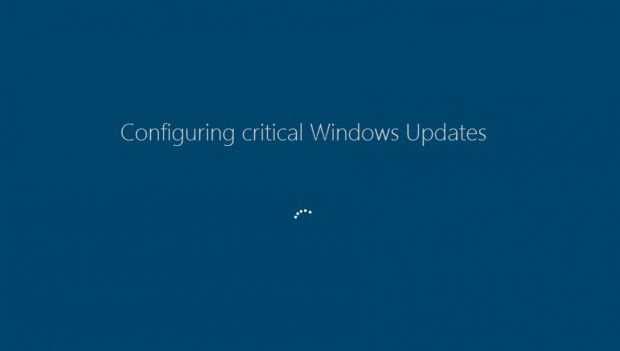
Fantom distributed as a fake Windows critical update
There are no details on Fantom's distribution. The method employed by crooks to plant the malicious file on the user's computer can be either via spam email or exploit kits.
Either way, the Fantom-infected file is named criticalupdate01.exe, and the crooks are using the "Windows Security Update" lure to fool users into running their malicious file.
When this happens, the ransomware springs into action by locking the user's screen and showing fake Windows Update graphics, with a fully functional percentage-based loading timer, just like on the original Windows Update screen.
Don't be fooled by this screen, because it's a trick, and under the hood, Fantom is encrypting your files. This temporary lock screen can be removed before it reaches 100% by pressing CTRL+F4, but this won't stop the encryption process.
According to MalwareHunterTeam, the ransomware uses classic ransomware encryption by locking files using an AES-128 key and then encrypting this key with a dual RSA key, with the private key stored on the crook's server, and a public key left on the user's PC.
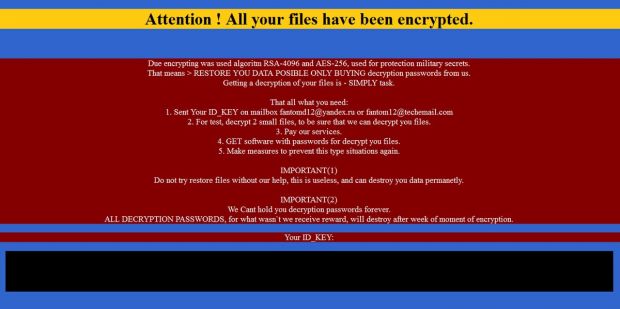
To get the private key and unlock their files, users have to contact the crook by email. The crook's email addresses are listed in the ransom note, displayed after the encryption process ends.
Fantom shows ransom notes in the form of HTML and TXT files, but it also changes the user's desktop with a custom screenshot containing the contact details.
At the end of all these operations, Fantom cleans after itself by running two batch scripts that delete its installation files.
 14 DAY TRIAL //
14 DAY TRIAL //