A fake WordPress plugin has been targeting the largest blogging platform in the world, researchers discovered.
Called WP-Base-SEO, the soft is a forgery of a legitimate search engine optimization plugin, called WordPress SEO Tools, security firm SiteLock writes.
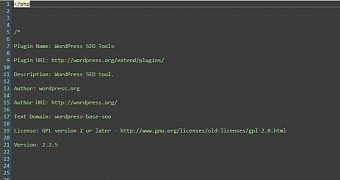
According to them, at first glance, the file appears to be legitimate, including a reference to the WordPress plugin database and documentation of how it works exactly. A closer look, however, reveals that the plugin has a malicious intent in the form of a base64 encoded PHP eval request.
Eval is a PHP function that executes arbitrary PHP code and it is frequently used for malicious purposes. It has become so abused, in fact, that php.net recommends against using it.
The malicious wp-base-seo plugin's directory holds two files. One of them, wp-sep.php uses different function and variable names depending on the install. The second, wp-seo-main.php uses native WordPress hook functionality to attach the eval request to the header of the website's theme.
At this point, the attackers have back-door access and can force sites to do what they desire.
"Some versions include an additional hook that runs after each page load. This means that anytime the theme is loaded in a browser, the request is initialized," SiteLock notes in the report.
Running undetected
Researchers have observed multiple sites that have been infected by the malware, but researching the Internet for the plugin name reveals no information. This likely suggests that this particular malware has gone largely undetected until now.
WordPress site admins are advised to run a malware scan and update the WordPress core, as well as all the themes and plugins, to the latest version. It is also advisable that, as a general rule, obscure plugins are avoided altogether.
"If you find a suspicious plugin in your /wp-content/plugins directory, it is best to delete the entire folder and reinstall a clean version of the plugin either in the WordPress admin dashboard or by downloading it directly from WordPress.org," researchers conclude.
 14 DAY TRIAL //
14 DAY TRIAL //