The WhatsApp team patched a critical security flaw in the Web-based version of their popular instant messaging application.
WhatsApp for Web is not as used as the mobile versions of the application, but around 200 million of the company's 900 million users have used it in the past.
As we previously wrote, WhatsApp for Web is constantly being updated to look as much as possible as the native app, mirroring content over the Web, as it's being exchanged via the mobile clients.
While most of the discussions are carried out via simple text messages, WhatsApp users can also transfer images, videos, audio files, map locations, and contact cards (in vCard format).
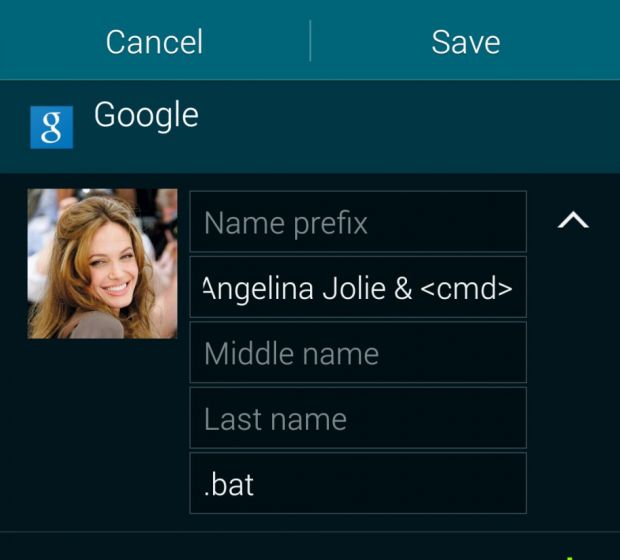
The security flaw resided in how WhatsApp for Web treated vCards
As Check Point's security researcher Kasif Dekel has recently discovered, a lack of security filters when exchanging vCards between clients, opened up WhatsApp for Web users to arbitrary code execution.
By adding malicious code to a vCard's name field, an attacker, thanks to the WhatsApp for Web vulnerability, could have triggered that code to execute when the user opened the file on his computer.
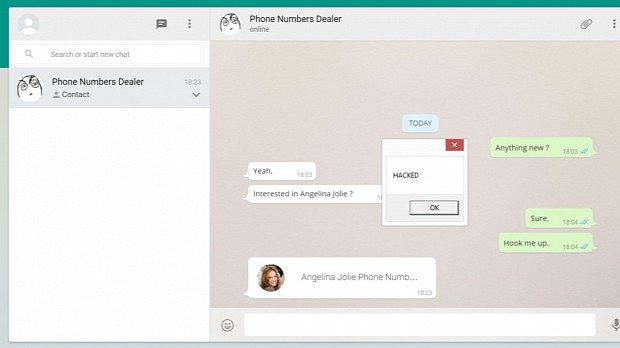
This meant that an attacker could have easily fooled unsuspecting users to load ransomware on their computer, take down the local firewall, or add the computer to a botnet via specially crafted malware, all by clicking a vCard sent by another WhatsApp user.
Even worse, since WhatsApp for Web failed to validate not only the vCard's content, but the file extension as well, Check Point security researchers were also able to send an .exe executable file without any problems.
WhatsApp fixed security flaw in less than a week
While changing the file extension of a vCard doesn't sound that dangerous, this security flaw could have opened the doors to various scamming and phishing campaigns on the service's users, if left unpatched.
By hiding code in the vCard and using the contact card's image field to add icons to messages, attackers could have easily made their messages more appealing to users, fooling them into downloading and executing the malicious code.
Because of this reason, after receiving the vulnerability disclosure from the Check Point team on August 21, by August 27, the WhatsApp team already upgraded their Web interface to prevent the vulnerability from being leveraged in the wild by attackers.
 14 DAY TRIAL //
14 DAY TRIAL //