Security researchers from Malwarebytes uncovered today a new trick used by malware distributors that rely on sneaky domain names that fool webmasters into thinking (malicious) code that mysteriously appeared on their site is responsible for powering a social sharing button.
For this trick to work, attackers must first hack into the webmaster's website. Malwarebytes says they've seen this happen on a series of Joomla and WordPress installations, which doesn't surprise us since this happens quite a lot lately.
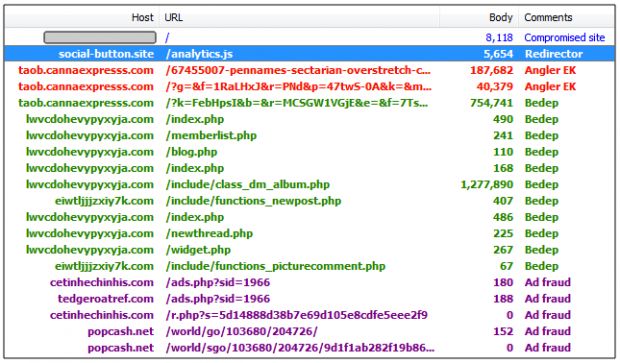
Once the attacker has compromised the site, he adds his malicious JavaScript call to the site's source code in the form of something like "http://social-button.site/analytics.js". Of course, other domains will also work (socialplugin.io, etc.).
If webmasters suspect anything, a quick inspection over the code might fool him into thinking he's looking at a social sharing plugin's JavaScript file.
Accessing the file directly in a browser yields actual JavaScript code with no malicious intent. When users access the infected site, this code gets loaded in their browser with the proper referrer settings, and the innocent code gets replaced by something more dangerous.
This malicious version of the so-called "social sharing analytics" code will redirect users through a series of intermediary points, eventually landing on a page hosting the Angler exploit kit.
If the user is using an outdated browser or outdated browser plugins, Angler will execute malicious routines and deliver the Bedep click-fraud malware.

 14 DAY TRIAL //
14 DAY TRIAL //