Two of the security vendors that investigated the first data breach at the Democratic Party, the DNC hack, have taken a look at the second incident, the DCCC episode, and have concluded that the same group is behind both attacks.
The whole Democratic Party cyber-drama started in mid-June, when CrowdStrike, a US-based security vendor, found evidence of two different cyber-attacks against the Democratic National Committee (DNC).
Last Friday, new reports surfaced about a second cyber-attack at the Democratic Congressional Campaign Committee (DCCC), a group inside the Democratic Party, tasked with gathering campaign funds for the party's presidential election campaign.
The Democratic Party hacking drama
The first attack, the DNC hack, was attributed to two cyber-espionage groups that penetrated the DNC servers at different times and were both linked to Russian state agencies, based on previous cyber-attacks.
The first DNC attack came last year, from a threat group called Cozy Bear (CozyDuke, APT29), while the second came from a group called Fancy Bear (Sofacy, APT28, Sednit, Pawn Storm, or Strontium), and happened in April 2016.
While both attacks were important, it was during the second attack, the Fancy Bear incident, that attackers managed to steal data from the DNC servers. This data was later leaked online by a hacker named Guccifer 2.0, whom many have suspected of being a sockpuppet for the Fancy Bear team.
There were many people who criticized the attribution of the attacks to the Russian government, but security researchers from at least four companies analyzed the malware and linked it to past Fancy Bear hacking campaigns.
Phishing site used in DCC hack has connections to past Fancy Bear assets
Now, a team formed of ThreatConnect and Fidelis Cybersecurity researchers has taken a look at the cyber-attack reported during the second attack, the DCCC hack.
According to their joint report, the companies say that a phishing site used in the DCCC hack was registered with an email address that had been used in the past to register numerous other domains used in phishing and other attacks by the same Fancy Bear group.
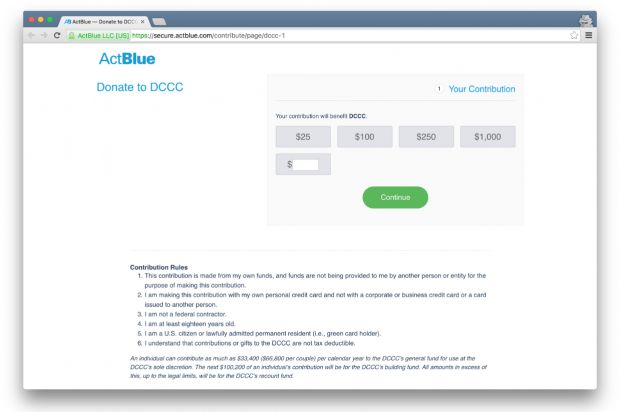
The domain they discovered was actblues[.]com, which is a letter shy of actblue[.]com, a payment handler that the DCCC was using to collect funds for the Clinton presidential campaign.
According to initial reports, the hackers managed to trick users into accessing this site by hacking the DCCC site and modifying the menu URL, linking to the donation page, replacing it with the one for the phishing site.
Phishing domain registered on the same day as the DNC hack report
Furthermore, the actblues[.]com domain was registered on the same day that CrowdStrike published its initial report on the DNC hack.
Researchers think that Fancy Bear hackers might have been scared off by the report and decided to choose another target to hack, shifting operations to the DCCC, with a brand new domain.
"This indicates that the domain was operationalized in less than a day," the investigators reveal. "This suggests that, after being outed, FANCY BEAR actors shifted their operation immediately to another target that might allow them to continue collection against Democratic figures involved in the U.S. election."

 14 DAY TRIAL //
14 DAY TRIAL //