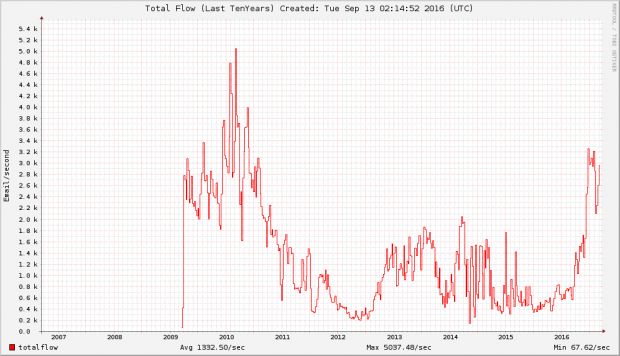
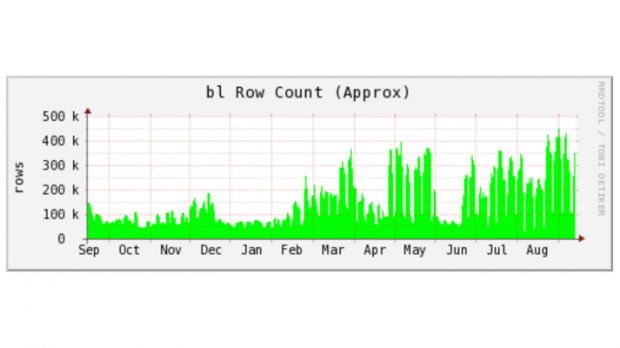
Spam levels around the world are returning to the massive numbers recorded in 2010 when overflowing email inboxes were one of the Internet's biggest problems.
A report published today by Cisco's Talos team highlights the fact that, since February this year, spam levels have been slowly growing from 200K messages per day to around 450K right now.
Shame on you, Necurs botnet!
Cisco puts most of the blame on the Necurs botnet, which they say is responsible for most of the junk email traffic today.
Even worse, this botnet that previously delivered only Russian dating and stock pump-n-dump spam has now changed strategy and is deploying messages with malicious files attached.
While Necurs took a small break in mid-June, right after the Lurk gang arrests, the botnet returned to form just three weeks after. In fact, Cisco says that this is the moment when the crooks behind Necurs changed their mode of operation and switched to spam floods delivering attachments.
Most of these files come boobytrapped with all sort of nasty malware, but mainly help propagate the Dridex banking trojan and variants of the Locky ransomware.
Detecting Necurs spam is hard, a constant fight
Providing some insight into how this botnet works, Cisco reveals why it's been so hard to detect all the botnet's bots and catch and stop spam campaigns in time.
Cisco's Jaeson Schultz explains that this huge botnet, one of the largest online today, never spams with all its bots at once.
"An infected host might be used for two to three days, and then sometimes not again for two to three weeks," Schultz says. "This greatly complicates the job of security personnel who respond to spam attacks, because while they may believe the offending host was subsequently found and cleaned up, the reality is that the miscreants behind Necurs are just biding their time, and suddenly the spam starts all over again."
The conclusion is that spam botnets are reaching the critical level at which they were in 2010, and we might need security vendors to bind together and work with law enforcement agencies to bring these new threats down.
If you're looking into more data about the Necurs botnet, Trustwave has recently published an in-depth report.
 14 DAY TRIAL //
14 DAY TRIAL //