The ElGato ransomware family, recently discovered by Intel McAfee researchers, targets Android devices. Specifically, it locks the user's device, encrypts their files, and even steals SMS messages when commanded.
The ransomware operates based on a control panel from which the crooks send commands to infected devices.
Intel McAfee researchers say that ElGato checks for new commands from the C&C server at regular intervals. These commands are sent to the ransomware in clear HTTP, without encryption.
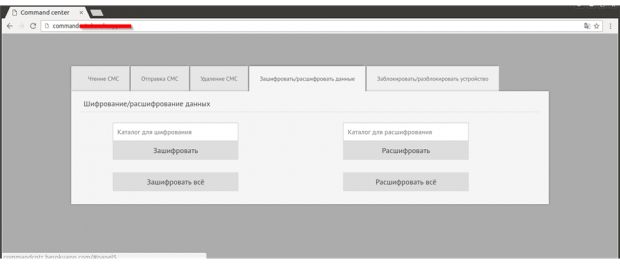
ElGato comes with an easy-to-use Web-based control panel
Some of the commands supported include the ability to forward and delete all SMS messages, send a message from the infected device, encrypt the files on the SD card, or encrypt files from at a specific path. All encrypted files will feature the .enc file extension at the end.
Additionally, the crook can also lock the user's screen and additionally order the ransomware to decrypt all previously encrypted files. This way, the ransomware serves as a decrypter after the user has paid the desired ransom.
In its current version, Intel McAfee experts say ElGato does not show a ransom note, nor does it ask for money, but merely shows a picture of a lovable cat whenever it locks the user's screen. Hence the ransomware name of El Gato, which means "The Cat" in Spanish.
ElGato is still under development
Since all communications occurred via HTTP, researchers were able to track down ElGato's C&C server, where they were surprised to find the botnet control panel open to exterior connections, no password required.
"This ransomware variant looks like a demo version used to commercialize malware kits for cybercriminals because the control server interface is not protected and includes in the code words such as 'MyDificultPassw,'" Intel McAfee security expert Fernando Ruiz noted. "McAfee Labs has informed the owners of the abused servers and has requested they take down the malicious service," he also added.
The overall low complexity of this threat sustains Ruiz's statements, meaning this is an unfinished product, not yet ready for broad distribution. Crooks will need to improve its encryption routine, deploy HTTPS for the C&C server communications, and protect the botnet control panel with a login field.

 14 DAY TRIAL //
14 DAY TRIAL //