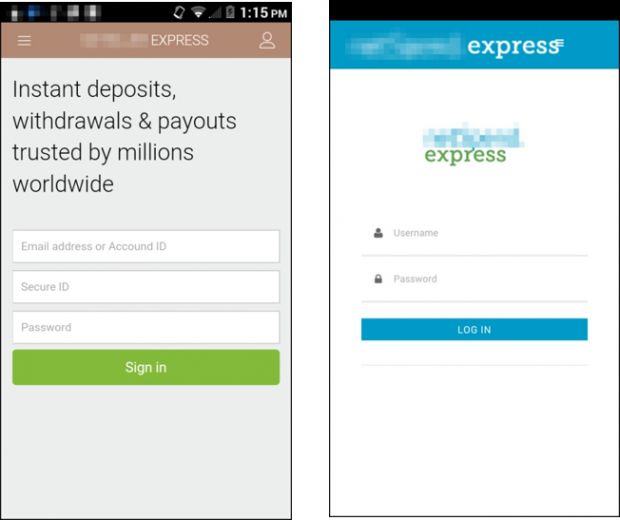
At least eleven malicious Android apps hosted on the Google Play Store are showing malicious overlays that are designed to steal login credentials for various financial applications.
These applications managed to end up on the official Android app store even if Google deploys a dual review process that involves automatic app code scanning and emulation via its Bouncer system, but also a partial app review check by its Play store employees.
The apps rely on the trust users have in Google's app store in order to lower user defenses and suspicion. Security firm PhishLabs were the ones that spotted, analyzed and reported these apps.
Malicious apps lack sophistication but are highly efficient
Experts say that these apps pose as official apps for various payment card companies and online payment sites but, in fact, are nothing but mere fakes.
Their mode of operation lacks any sophistication, and PhishLabs experts say the techniques are quite trivial, yet work because users don't show the same level of scrutiny for apps downloaded from the Play Store as they do with apps installed from other sources.
The crooks' preferred method of attack is to launch a WebView component (stripped down browser with no UI) and ask the user to log into the app.
The app collects all user credentials and funnels them to the crooks' server in a classic phishing form grab attack.
Crooks uploaded the apps on the Play Store at the beginning of the year
Researchers said that clues left in the source code of these apps led them to believe the same criminal group is behind all of the phishing apps.
These apps appeared at the start of 2016, contained only the phishing code and nothing else, and some of them used look-alike domains used by cryptocurrency companies. PhishLabs says that no app ever showed cryptocurrency theft behavior.
"While the inner workings of these attacks are not sophisticated, the repercussions of functional mobile phishing applications finding their way into legitimate mobile app repositories are significant," Joshua Shilko, Security Threat Analyst for PhishLabs explained. "In Google's defense, they are not the only company who struggles to detect these mobile phishing applications."
Softpedia has reached out to PhishLabs to inquire if Google removed the apps from the Play Store.
UPDATE: Mr. Shilko provided the following answer to our inquiry: "At of the time of publication, all of the applications referenced in the post had been removed except for one. When PhishLabs detects an attack on our clients, we work with the responsible providers to have the infringing content removed."

 14 DAY TRIAL //
14 DAY TRIAL //