EduCrypt is a new ransomware variant, first spotted by AVG's Jakub Kroustek, which doesn't ask for money as ransom, but locks the user's files and then provides them with a way to decrypt their data, only to teach them a lesson.
This ransomware is based on Hidden Tear, an open source ransomware variant that was published last year and came with an encryption backdoor.
EduCrypt includes a stripped-down version of Hidden Tear, with minimal features, just to ensure the basic file locking process works.
EduCrypt is very simplistic, only targets a handful of files
The ransomware will only encrypt files on the user's Desktop, and in the Downloads, Documents, Pictures, Music, and Videos folders. EduCrypt only locks 41 file types, a relatively low number, and uses a simple AES encryption to lock the user's files.
There's no C&C infrastructure, and the encryption key is saved locally. Once the encryption finishes, the ransom note is placed on the user's desktop. The ransom note reads:
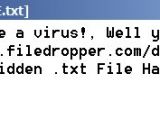
“ Well hello there, seems you have a virus!, Well you are going to get the cryptor which is here [REDACTED URL] Don't Download Random [expletive] On The Internet A Hidden .txt File Has Been Created With The Decrypt Password! Find It!.. ”
According to Lawrence Abrams, this hidden file is always in the same location, at %UserProfile%DocumentsDecryptPassword.txt, and contains the same decryption password: HDJ7D-HF54D-8DN7D.Ransomware for educational purposes
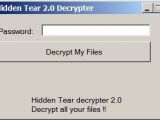
Even if EduCrypt's author provides a link to a legitimate Hidden Tear decrypter, but hosted on a random file hosting site, you'd probably be safer if you download Demonstlay's Hidden Tear decrypter just in case. To be fair, EduCrypt's coders just told you to stop downloading random [expletive] off the Internet, so download the Hidden Tear decrypter from its original source, just to be safe.
Kroustek has told Softpedia that EduCrypt is distributed via an applications named "Skype Color.exe" and "skypetool.exe" via file sharing sites.
If you've been infected with EduCrypt, you've just dodged a bullet, and you can still recover your files, something that Locky, Cerber, or Crysis users can't afford right now. At this point, you should learn your lesson, as the EduCrypt authors wanted, and stop downloading and running random files off the Internet.
How to name educational #ransomware? #educrypt? Found samples encrypting files and providing free decryptor and key. pic.twitter.com/KbiRvHXuRH — Jakub Kroustek (@JakubKroustek) June 26, 2016

 14 DAY TRIAL //
14 DAY TRIAL //