The Dyreza banking trojan is slowly evolving into an all-business trojan after it changed in time to target companies that activate in different economic fields.
While in the beginning the trojan was highly efficient at exfiltrating credentials for online banking accounts, Dyreza's creators have evolved their methods, mainly to stay ahead of cyber security solutions, but also to broaden their scope and be able to steal information from a larger target base.
Dyreza, first detected in the summer of 2014, has been observed in the past targeting online banking services, job hunting portals, file hosting websites, domain registration services, website hosting tools, file hosting solutions, tax services, and online retail shops.
A new campaign targeting warehouses, supply chains, and orders fulfillment companies
Proofpoint researchers are now warning of a new campaign, which they first spotted on September 17 and has targeted over 20 companies involved in the warehousing and orders supply chain sector.
The Dyreza trojan seems to have been modified specifically for this campaign, coming hard-coded with login credential triggers for supply chain software manufactured by companies like Apple, Iron Mountain, OtterBox, Badge Graphics Systems, Four51, Aero Fulfillment, and a few others.
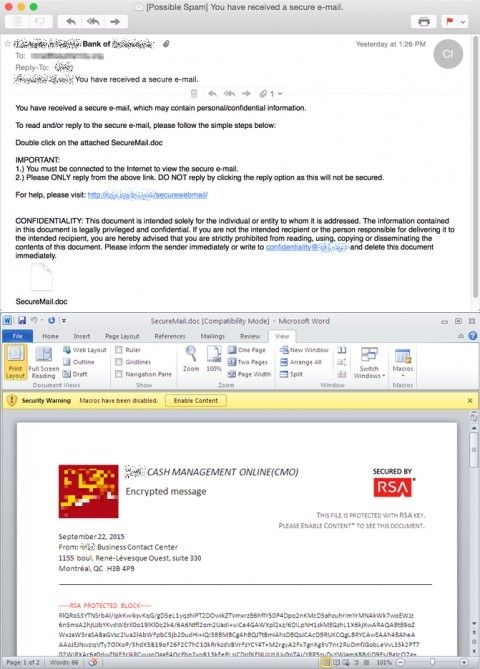
In this most recent campaign, infection occurs via classic spam emails. Victims will receive an email with the "You have received a secure e-mail" subject line, that also comes with an MS Word file attachment.
Dyreza infects users via malicious email attachments
The email also instructs users to open the attachment, only if they're connected to the Internet. Once the Word document opens, users are asked to activate the software's "Macros" feature to be able to view the encoded content.
This is because the file is rigged to run a Word macro which downloads a payload on the user's computer. This secondary payload usually downloads the Upatre downloader, a malware string specialized in downloading and installing other malware.
Doing its due diligence, Upatre downloads and installs the Dyreza malware.
Once on the infected machine, Dyreza stays hidden, waiting for users to open one of the "theft trigger" URLs. When this happens, all captured data is sent to its C&C server.

 14 DAY TRIAL //
14 DAY TRIAL //