It has now become official, and it appears that the Dridex botnet that has been distributing banking trojans for years, has now changed its profile entirely and is spreading ransomware instead.
Initial reports on this topic came from Palo Alto researchers, who at the middle of February noticed that the Dridex botnet has stopped delivering its infamous and highly dangerous banking trojan, of the same name.
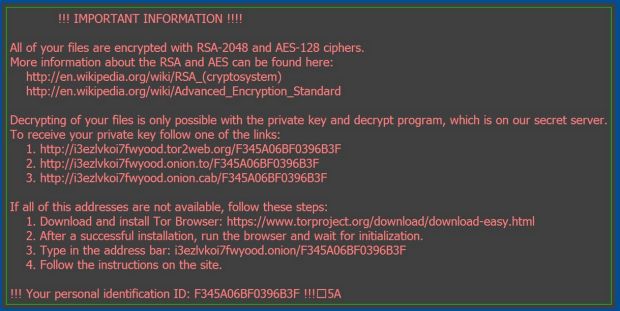
Researchers noticed at the time that the botnet's operators started pushing a new type of ransomware variant, which was later named Locky, after the extension it adds to all the files it encrypts.
Locky was a success from the get-go
Dridex botnet operators have a huge experience in delivering malware, operating since 2014, and some of them even before that as part of Gameover Zeus, another infamous top-3-level banking botnet.
Their experience at pushing massive amounts of spam showed right away, as Locky quickly made victims around the world, becoming as dangerous as TeslaCrypt or CryptoWall.
Almost a month after botnet operators started their ransomware spree, it appears that this was more than a test, and the group is making the complete switch from the banking sector to ransomware operations.
Dridex's banking trojan seems to be a thing of the past
"Our Spam Research Database saw around 4 million malware spams in the last seven days, and the malware category as a whole accounted for 18% of total spam arriving at our spam traps," says Trustwave SpiderLabs researcher Rodel Mendrez.
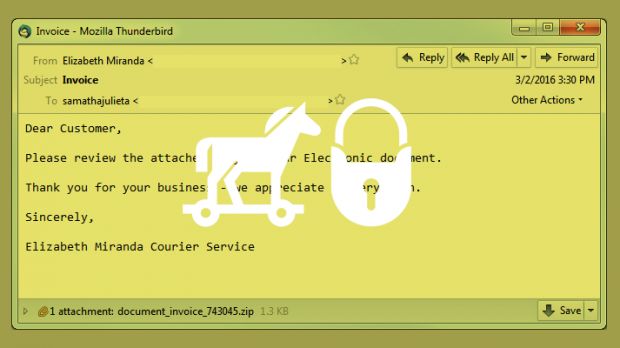
Of these, the researcher says that a large part is coming out of the old Dridex botnet infrastructure. The spam emails include a ZIP file that, when executed, downloads a malicious JS file that downloads and runs the Locky ransomware.
There doesn't appear to be any trace of the older Dridex banking trojan anymore, with the spam campaign giving up on delivering Word files that include macro automated actions that previously installed the banking trojan.
The arrest of Dridex's mastermind might have had something to do with it
One of the reasons the group might have given up on targeting financial institutions is the arrest and subsequent US extradition of Andrey Ghinkul, 30, from Moldova, considered to be the mastermind behind the entire operation.
While law enforcement thought Dridex would go down for good after his arrest, the group simply decided to change MO and focus on more simpler monetization schemes like ransomware.
Benefiting from a massive infrastructure already put in place during their previous operations, Dridex's Locky has become a major player on the ransomware scene just a few days after it launched and common sense dictates that it will remain so until more group members are arrested and the botnet is sinkholed.
 14 DAY TRIAL //
14 DAY TRIAL //