A mysterious hacker is having a laugh at Dridex's expense once again after he recently hacked the malware's botnet and replaced the Locky ransomware with an empty file that contained the phrase "Stupid Locky."
Dridex is the name of a banking trojan that's been wreaking havoc among users for the past years. The name of this malware is also used to describe the server infrastructure from which the banking trojan spreads, and where it sends all the stolen financial data.
When the criminal group behind Dridex diversified its operations during the past year, despite distributing other malware besides the banking trojan, the botnet's name remained.
The most recent malware which Dridex operators started distributing is called Locky and is one of today's most complex and most predominant ransomware variants.
Stupid Locky is stupid, says unknown hacker
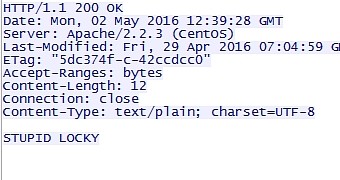
Avira security experts claim that during the past days, they've observed the number of Locky infections go down. The reason behind this appeared to be a malformed ransomware binary file, the file which is downloaded automatically using a JavaScript file by infected victims from the botnet's servers.
The company's malware analysts had a look at this file and found that instead of the Locky ransomware source code, this file only contained two words: "Stupid Locky."
The security firm thinks that someone hacked the Dridex botnet once again and intentionally replaced the Locky ransomware with this harmless file.
The incident does not appear to be a "test"
Exactly three months ago, Avira also revealed that a white hat hacker had also hacked the Dridex botnet and replaced the Dridex banking trojan with an installer for the Avira Free Antivirus.
The incident happened again at the start of April when security firm buguroo also managed to hack their way into the admin panel of one of Dridex's sub-botnets. In that case, the company retrieved data stolen by the criminal group and even compiled a nice report on Dridex's mode of operation.
"I don’t believe that cybercriminals themselves would have initiated this operation because of the potential damage to their reputation and income stream," Avira's Sven Carlsen noted. "I also wouldn’t say that “Locky is dead” after this operation. But after the examples of Dridex and now Locky, it shows that even cybercriminals, masters of camouflage, are also vulnerable."
UPDATE: MalwareTech now reports the same thing, but with a more expletive message regarding Dridex.
 14 DAY TRIAL //
14 DAY TRIAL //