Malwarebytes security researcher Hasherezade has dissected the most recent version of the DMA Locker ransomware, which she claims made important strides in improving quality overall and getting ready for a massive distribution campaign.
The first version of DMA Locker appeared this past January. Technically, the ransomware was a joke, coming with hilarious flaws such as the decryption key being hardcoded in the ransomware binary, and the ransomware working as a decrypter.
Researchers had no problem crafting a decrypter that recovered user files. The same thing happened with DM Locker 2.0, which appeared almost a month later, at the start of February. Nevertheless, researchers noted an improvement over the first version.
DMA Locker 3.0 and 4.0 are undecryptable
Version 3.0, which appeared at the end of February, was the first one that malware analysts couldn't crack. It also featured the first signs of a better encryption system.
Development on DM Locker then took a big break until a few days ago, when Hasherezade noticed for the first time DMA Locker 4.0. This new version features many improvements, which take DMA Locker out of the mediocre class of ransomware families and place it nearer to the top.
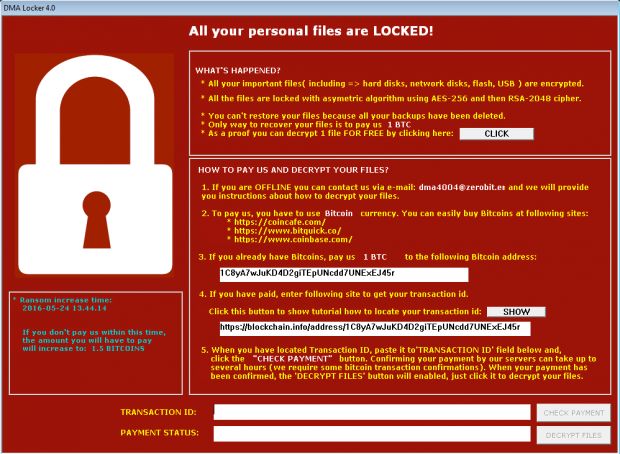
The ransomware, which always worked offline, now uses a C&C server. Instead of a single encryption key hardcoded in the ransomware itself, DMA Locker now generates unique AES encryption keys for each file and encrypts these AES keys with a public RSA key obtained from the C&C server.
To decrypt all the locked files, the user needs the other part of the RSA key, called the private RSA key, which never touches the user's computer. To obtain this key, users need to contact the DMA Locker authors. This is another major change from the previous ransomware versions.
DMA Locker now works with a C&C server
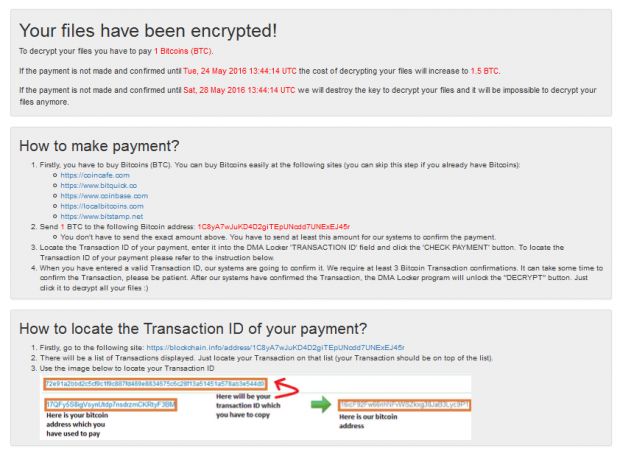
Previously, the ransomware required users to send an email to the author to obtain the decryption keys. Now, DMA Locker 4.0 has been fully automated and even comes with its own website where users can pay their ransom, just like the other ransomware big boys.
Yet, this website is not fully functional, and Hasherezade says that the free test decryption doesn't return the decrypted file. Additionally, the website is hosted on a public IP, not the Dark Web, making it susceptible to takedowns.
Even worse (or better, depending on the point of view), the website is hosted on the same IP as the C&C server, so taking down this server will take down the crook's entire operation in one quick swoop.
Compared to its previous versions, DMA Locker made huge leaps, getting closer to how professional threats like Locky or CryptoWall operate. It is not yet there, but once this happens, Hasherezade believes we're going to see a massive distribution campaign.
"The recently observed changes suggest that the product is preparing to be distributed on a massive scale," the Malwarebytes analyst wrote yesterday. "Few important things got automated. Distribution is now exploit kit based - that makes it reach much more targets. Purchasing a key and managing payment is supported via dedicated panel - no longer human interaction is required."

 14 DAY TRIAL //
14 DAY TRIAL //