Security researcher Chris Vickery has gone public with details about two mobile apps that were leaking information about all their users. The two apps are Hzone, a Tinder clone dating app for people with HIV, and iFit, a health tracking application.
According to Mr. Vickery, the Hzone dating app was providing access to its database to anyone with an Internet connection. The issue is well known and relates to administrators using the default MongoDB configuration file, which leaves the database administration port open to outside connections.
Previous reports on this issue revealed that almost 1.2 petabytes of information were exposed online via improperly configured MongoDB applications.
Tinder clone for HIV people leaks user data
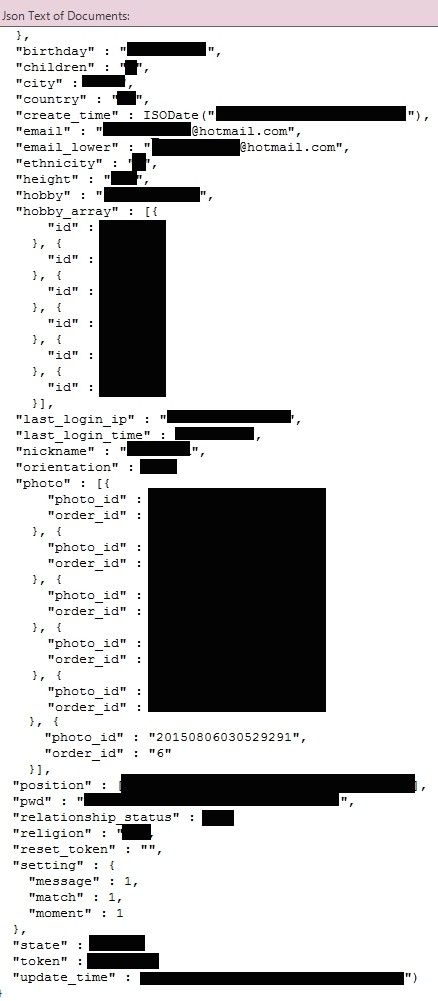
Mr. Vickery discovered that HZone was disclosing information about 5,027 users, which included details such as date of birth, religion, relationship status, country, email address, ethnicity, height, last login IP address, username, orientation, number of children, password hash, nicknames, political views, sexual life experiences, and avatars.
Even worse, the application also logged private conversations, which were also accessible via the leaking database.
To make the data leak an epic one, Hzone premium subscribers also had their full name, postal address, phone numbers, and credit card data exposed, allowing anyone to make fraudulent purchases on their behalf.
Hzone: I suppose you and your family members don't want to get HIV from us?
The company behind Hzone was notified of the breach, but answered Mr. Vickery's emails only after the reporters from DataBreaches.net were brought in to assist in the research.
The data leak was eventually plugged, but at one point, the email conversations got really silly, with the Hzone developers saying (via Salted Hash):
"Why do you want to do this? What's your purpose? We are just a business for HIV people. If you want money from us, I believe you will be disappointed. And, I believe your illegal and stupid behavior will be notified by our HIV users and you and your concerns will be revenged by all of us. I suppose you and your family members don't want to get HIV from us? If you do, go ahead."
iFit also leaks private user details, health information
But Vickery didn't stop here. He also disclosed, via DataBreaches.net, that another application, iFit, which lets users track their workouts and their health, leaks data in the same way.
This app leaked name, username, password, date of birth, current weight, target weight, height, gender, measurement system, activity level, fitness goal, intensity level, and just like Hzone, if you attached your credit card or Facebook account to your iFit profile, it would leak that information as well.
iFit developers responded to Vickery's emails only after the researcher got reporters to help him out, and took down the server leaking that particular information right away, which they said was only an internal system that contained real user data, used only for testing purposes.
UPDATE: In another data leak discovered by Mr. Vickery, about MacKeeper, it was revealed that iFit exposed data about 576,000 accounts.
We also corrected the article with details about the iFit data leak disclosure timeline, via Dissent, the DataBreaches.net admin.
 14 DAY TRIAL //
14 DAY TRIAL //