Just like Lenovo did at the beginning of the year, Dell has included a root certificate on some of its laptops that can be extracted by malicious actors and used for MitM (man-in-the-middle) attacks, passing dangerous content as legitimate.
Digital certificates are files used to sign software as coming from a legitimate source. Root certificates are high-privilege digital certificates that are used to sign entire hierarchies of certificate structures and are usually issued by CAs (Certificate Authorities), companies that go through a large number of security checks before being granted this title.
Many large software manufacturers are all CAs themselves. This includes Google, Apple, HP, Oracle, Microsoft, and, of course, Dell.
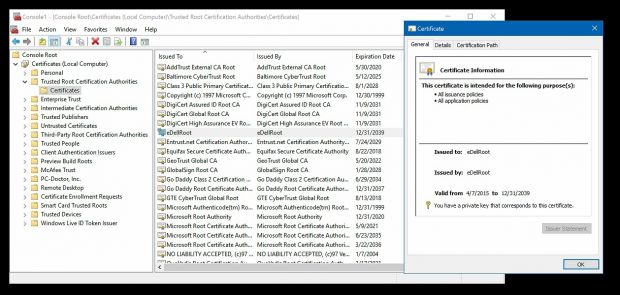
The problem is that, according to the discoveries of a Reddit user, Dell has been shipping a few of its laptops with such a high-level root certificate.
eDellRoot allows malicious actors to pass dangerous content as legitimate
This root certificate, named eDellRoot, can be extracted with special tools from the laptop's filesystem and then used to sign malicious software, passing it as a safe source. Its usage is not limited to PC software, but can also be used to sign Web-server connections.
While this wouldn't be a problem if eDellRoot contained a private key unique for each computer, this isn't the case.
"After briefly discussing this with someone else who had discovered this too, we determined that they are shipping every laptop they distribute with the exact same root certificate and private key, very similar to what Superfish did on Lenovo computers," said rotorcowboy, the Reddit user who discovered the issue.
The Lenovo Superfish fiasco, all over again
Last February, the very same thing happened to Lenovo, when security researchers found a root certificate coming preinstalled on various laptop lines. That root certificate was used for a browser extension that inserted ads in the user's Web pages. The purpose of Dell's certificate is unknown.
According to early verifications, the certificate started appearing on Dell laptops in August, long time after the Lenovo fiasco, which means somebody at Dell was stupid enough to think that pre-installed root certificates were still a good idea.
Users are reporting that only recent versions of Dell XPS 15 laptops, M4800 workstations, and Inspiron desktops and laptops seem to be plagued by this problem.
We'll be back with more news as the story unfolds.
UPDATE: Dell was quick to respond and said that it would stop delivering laptops with the eDellRoot certificate installed. According to company representatives, the certificate was included to power a customer support application installed on the laptops.
A tool to test if users are vulnerable has also popped up online. Security researchers say that all users using Web browsers are vulnerable, except those using Firefox.

 14 DAY TRIAL //
14 DAY TRIAL //