A recent research paper shows that most Cloud-Based Security Providers (CBSP) are ineffective in protecting websites from DDoS attacks, mainly because they cannot entirely hide the origin website's IP address from attackers.
Most cloud-based security solutions work by changing a website's DNS settings to place itself between the attackers and the target website.
The problem is that this type of DDoS mitigation can be easily bypassed if the attackers know the website's origin IP, in this case being able to send the DDoS traffic directly to the IP, bypassing the mitigation service.
There are eight methods through which attackers can obtain a site's origin IP address
As five security researchers from Belgium and the US are claiming, there are eight methods through which these mitigations services can be bypassed.
Four of them have already been widely discussed after Allison Nixon and Christopher Camejo presented them at the Black Hat USA 2013 security conference, but the researchers also found four new ones.
The four older techniques of obtaining a website's origin IP address rely on hackers searching through historical Web traffic databases, in DNS records, subdomains that resolve to the main domain directly, and the site's own source code.
On top of these, the researchers also found that the origin IP can also be discovered when the main website triggers outbound connections, via SSL certificates, via sensitive files hosted on the website's server, and during migration or maintenance operations on the mitigation service itself, which leaves the target website temporarily exposed.
During their studies, the researchers scanned 17,877 websites for six months, and found out that 71.5% of the sites revealed the origin IP address, in most cases through the FTP subdomain.
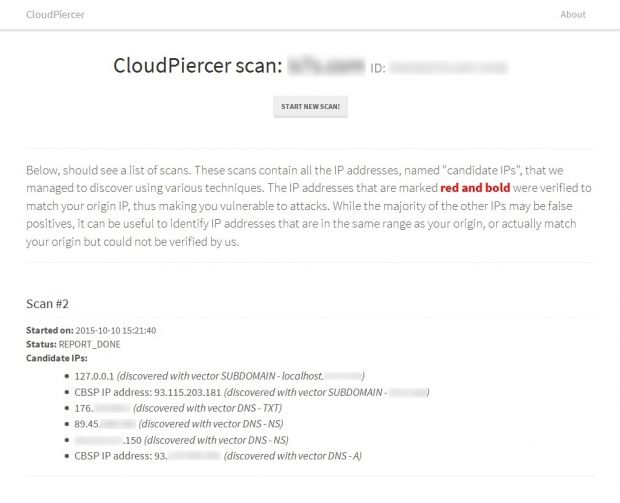
Enter CloudPiercer, an automated origin-IP detection system
To help webmasters identify problems with their own websites, the researchers put together CloudPiercer, a tool that compares a version of the website obtained from the real IP address, with one obtained through the cloud mitigation service.
"Complete mitigation of origin exposure is hard, as administrators are required to fully understand the potential risks and comprehensively address all vulnerabilities in order to fully prevent an attacker from circumventing the CBSP," say the researchers. "However, a tool similar to CloudPiercer could be deployed by CBSPs to proactively scan their client's domains for exposed origins, creating awareness and helping administrators fix specific vulnerabilities."
The full Maneuvering Around Clouds: Bypassing Cloud-based Security Providers report is available for download. Below is a sample CloudPiercer report.
 14 DAY TRIAL //
14 DAY TRIAL //