There are signs leading to the conclusion that the infamous Dark Seoul advanced persistent threat (APT) group may have resurfaced and is carrying out a new series of attacks.
Dark Seoul, also known under the name of Operation Troy, is a cyber-gang linked to North Korea that had terrorized South Korean for four years, having launched various attacks against the country's government, military, and broadcasting industry.
Multiple security vendors like McAffee, Symantec, Trend Micro, and Sophos brought its activities to light in 2013, and soon after the group went dormant.
Today Palo Alto Networks, a California-based security vendor, is reporting that its staff has detected new activity that closely resembles Dark Seoul's normal modus operandi.
Because this new campaign targets European companies, Palo Alto is still reluctant to call it a full Dark Seoul revival, but there are enough clues in the group's activity to do so.
New Dark Seoul campaign targets European businesses
According to the security researchers, this new Dark Seoul campaign started in June of this year and is targeting the transportation and logistics sector in Europe, with the initial attack hitting a company in the industrial control systems sector.
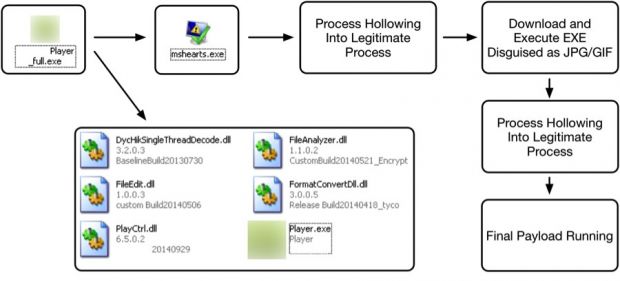
The infection steps were as usual, via spear phishing campaigns. For this particular case, attackers used a trojanized-version of a legitimate video player installation package.
The malware used with this package is a new variant meant to account for the technical updates to Windows software that occurred during the past two years when the group was dormant, but its behavior was just as in previous Dark Seoul campaigns.
"There are obvious similarities in the malware used, as well as other tactics, but there are also some obvious differences," say Bryan Lee and Josh Grunzweig from Palo Alto. "The similarities in tactics however, do seem to outweigh the differences, and it is highly likely this is the same group or groups responsible for the original Dark Seoul/Operation Troy attacks, but with a new target and a new campaign."

 14 DAY TRIAL //
14 DAY TRIAL //