A severe vulnerability disclosed last month in D-Link's DCS-930L Network Cloud Camera has been found to affect over 120 other D-Link products because the company's engineers reemployed the same vulnerable component across the different firmware versions used with their devices.
Last month, security researchers from Senrio discovered that D-Link DCS-930L cameras contained an RCE (remote code execution) vulnerability that allowed crooks to execute arbitrary code on the device.
The company created a proof-of-concept exploit that reset the webcam's password to highlight the issue. Stephen Ridley, the security researcher who discovered the issue, says that he found the same vulnerable component used in over 120 other D-Link products that range from access points to routers, and from data storage systems to modems.
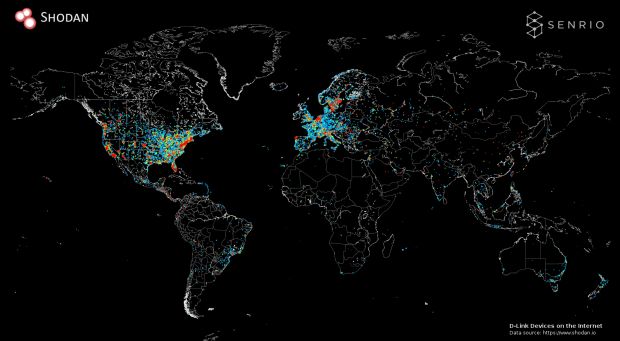
Over 400,000 D-Link devices currently available online
Since the RCE vulnerability can be exploited via a network connection, any vulnerable D-Link device that is reachable via a ping is potentially in danger.
In total, the researcher claims that over 400,000 D-Link products are currently available online.
In an interview ahead of SecurityWeek's 2016 ICS Cyber Security conference, where he's scheduled to be present, the researcher said that his original password reset code could be replaced with any type of exploit, capable of any action.
All an attacker needs to do is to adapt the original exploit to the firmware of the D-Link device they want to target. An attacker only has to change the memory values where the exploit needs to run in order to target the vulnerable component within the device's specific firmware.
IoT botnets are the new hacker must-have
Last week, Sucuri revealed the existence of a 25,000-strong botnet comprised of compromised CCTV cameras.
This botnet was built based on vulnerable firmware code shipped by the same Chinese vendor to over 70 companies. The very same scenario could now repeat using D-Link devices.
Hacking outfits like Lizard Squad have built a reputation based on botnets of infected IoT devices capable of launching massive DDoS attacks.
D-Link has promised to fix all issues, but firmware upgrades for IoT devices are notoriously challenging and slow. By the time someone's grandma figures out how to apply a firmware update, that D-Link device will have already been part of a few hundred botnets.

 14 DAY TRIAL //
14 DAY TRIAL //