Santa-APT is a new cybercrime syndicate that developed malware to spy on its targets using Christmas-themed desktop and mobile apps.
The group was discovered by CloudSek, a SaaS-based security vendor that was initially monitoring a hacking group peddling a trojan on the black market.
This trojan targeted desktop devices and included quite advanced exfiltration capabilities, along with support for air-gapped systems (USB drives). The trojan was capable of stealing files from the local computer and making screenshots.
Desktop malware linked to software company from South Asia
CloudSek followed through on its investigation and uncovered that the trojan was sending all stolen data to a particular C&C server. The company's security researchers breached the server and found that its operators amassed more than 120 GB of stolen data.
For each victim, the trojan would create a different folder on the C&C server, where it sent data. The content of the folder also included two directories for voice recordings and keylogger data. CloudSek researchers claim that no such functionality exists in the trojan, so for now, the malware still seems to be a work in progress.
The security researchers tracked down the server's operators and found out the server was rented by a company from South Asia. They declined to name it, and only referred to it as Santa-APT.
The company also developed spyware for mobile devices
According to their subsequent investigation, the researchers discovered that the company was diversifying its activities and was hiring mobile developers. Further research revealed a mobile malware piece linked to the same company.
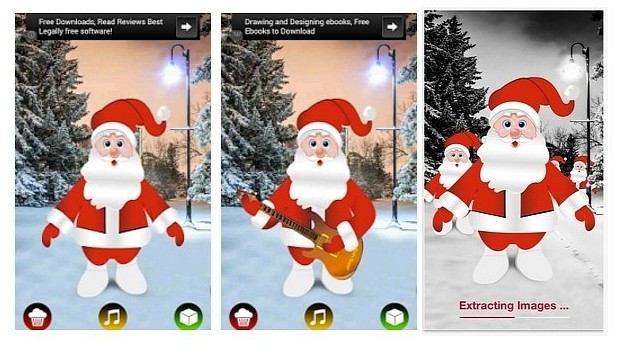
The malware had advanced spying capabilities and was distributed via Christmas-themed applications on both Android and iOS platforms. CloudSek did not reveal the name of the apps.
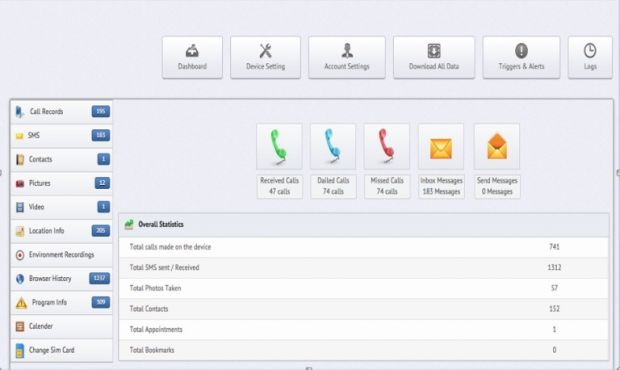
According to their analysis, this mobile malware was capable of stealing contact lists, SMS messages, call records, location info, calendar data, media files, browser history, SIM card and phone details. Additionally, the mobile malware was also able to tap into the phone's microphone and camera to make environment recordings.
CloudSek security researchers detected around 8,000 such infections, and also tracked down the mobile malware's backend panel.
We have contacted CloudSek for more details about the name of the company and the infected apps.

 14 DAY TRIAL //
14 DAY TRIAL //