Security researchers have discovered a new ransomware family named cuteRansomware that uses Google Docs to store information regarding infected victims.
The origin of this malware seems to be yet another ransomware experiment that was foolishly open-sourced on GitHub a few months back.
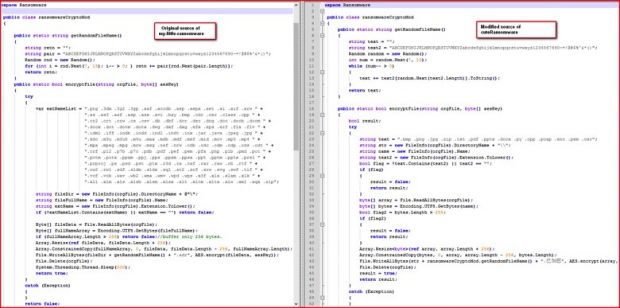
cuteRansomware based on open-source ransomware experiment
The project, named my-Little-Ransomware, is an "easy ransomware module base on csharp," as described by its creator, Chinese developer Ma Shenghao.
As it happened with the Hidden Tear and EDA2 projects open-sourced by Turkish security researcher Utku Sen, it didn't take long for crooks to use the my-Little-Ransomware code to create their own versions of ransomware.
The first ones were spotted in mid-June by AVG security researcher Jakub Kroustek, who immediately pointed out that this new ransomware used Google Docs to store its encryption keys.
A few days back, security firm Netskope saw a different ransomware variant, also based on the my-Little-Ransomware GitHub project. They named this one cuteRansomware because of the crook's usage of the "cuteRansomware" string all through his code. [UPDATE: We were told that cuteRansomware infections actually first appeared in mid-June as well.]
cuteRansomware seems to be targeting Chinese-speaking users only
From the get-go, researchers spotted that all code comments were written in Chinese, and so was the ransom note, hinting at a limited distribution model that at the time targeted only Chinese-speaking users.
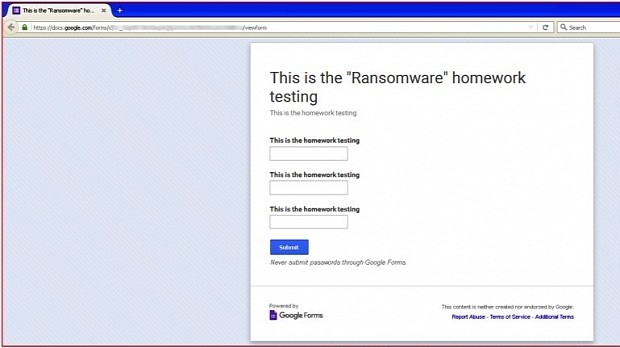
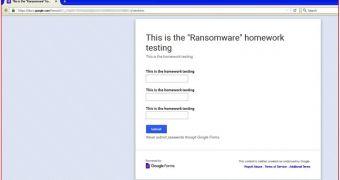
After a closer look at the code, as with the version spotted by the AVG researcher, this variant also used a Google Docs form as its C&C server.
cuteRansomware was infecting computers, generating the RSA encryption key, and then sending the key to the Google Docs form via HTTPS.
Researchers noted that, compared to the original GitHub project, this version of the ransomware targeted for encryption a smaller number of files, which is quite peculiar since this reduces the ransomware's ability to do damage on infected systems.
cuteRansomware uses .encrypted file extension (in Chinese)
Affected users can spot cuteRansomware infections by the lack of a ransom screen. cuteRansomware only shows a popup text file with the ransom note written in Chinese. Additionally, all encrypted files will have the ".encrypted" (in Chinese) extension added at the end.
"At the time of writing this blog, the form was still available on the Google Docs," said Netskope's Umesh Wanve. "[W]e have notified Google’s security team about this."
Malware that hides its C&C servers on cloud services is not new by any means. Last December, FireEye discovered the LOWBALL backdoor trojan, which used Dropbox as a C&C server.
 14 DAY TRIAL //
14 DAY TRIAL //