A ransomware family called CTB-Faker tries to pass as a more famous variant called CTB-Locker and lies to users about using strong encryption when it actually does nothing more than to move all the victims' data inside password-protected ZIP archives.
The good news is that this ransomware is decryptable, albeit via a complicated process for which regular users need to request assistance.
The second good news is that Lawrence Abrams of Bleeping Computer has volunteered to assist users with the decryption process for free.
CTB-Faker spread via adult websites
According to technical analysis from Bleeping Computer and Check Point, CTB-Faker is currently distributed via adult websites promoting private striptease dance videos.
Users are encouraged to download a ZIP file, which contains an executable. Running the executable starts the CTB-Faker ransomware, which will slowly move files to a password-protected file at "C:Users.zip."
To move the files and then password-protect the archive, CTB-Faker uses the WinRAR application. Once the ransomware creates this file, it forces a computer restart and then shows the ransom note after the user logs in.
Crooks have made serious money from their CTB-Faker campaign
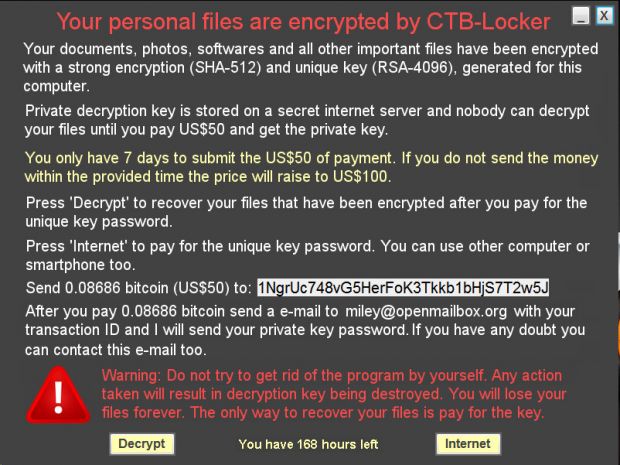
The ransom note is specifically designed to look like the same ransom note used by the more famous CTB-Locker ransomware. The reason for posing as another piece of ransomware is to discourage users from resisting making the ransom payment.
The strategy seems to be working, as Abrams reported discovering one Bitcoin address used for the CTB-Faker ransom note that received 577 Bitcoin (~$381,000) in payments.
It is not confirmed that all the Bitcoin funds came from CTB-Faker payments, but taking into account that the ransomware authors ask for 0.08 Bitcoin (~$50) per infected PC, that would have implied CTB-Faker infected over 7,200 users. Nevertheless, for such a simplistic ransomware variant, crooks seem to have made a return on their investment.
Decryption is possible on one condition
CTB-Faker's ransom note claims that the ransomware uses a combination of SHA-512 and RSA-4096 to lock files, but in reality, the encryption is AES-256, the standard encryption used to lock files inside a WinRAR archive.
The AES-256 encryption key (WinRAR password) is hard-coded inside the executable file found in the ZIP file users initially downloaded from the adult sites. If users still have that file around, they can contact Abrams for his help in extracting the ZIP file's password.
Previously, there were other two ransomware families that locked files inside password-protected archives. These were Bart and CryptoHost (Manamecrypt), both decryptable as well.

 14 DAY TRIAL //
14 DAY TRIAL //