Pranksters around the world will be happy to find out that there's an easy-to-exploit security bug in the ARRIS (formerly Motorola) SURFboard SB6141 modem that attackers can use to reset and/or factory reset the devices.
The issue solely affects the SURFboard SB6141 model, but the flaw's severity is exacerbated by the sheer numbers of these models currently deployed, which ARRIS estimates to be over 135 million.
As security researcher David Longenecker explains, these cable modems have an unprotected Web-based administration panel that everyone on the local network can access by going to 192.168.100.1.
Attackers can reset modems without needing user interaction
The lack of a password when accessing the modem's most sensitive part means that an attacker can use the admin panel's IP inside scripts to automate attacks.
But what to attack? While tinkering with modem settings might be a good point to start, that's generally useless since no real damage can be done. Except in two cases.
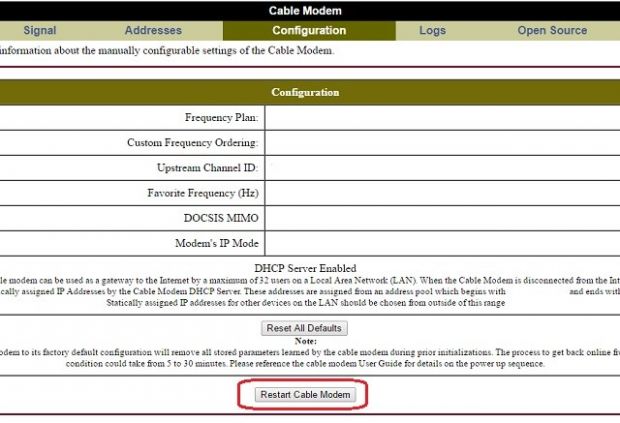
The modem's admin panel includes two controls. One is the "Reset Cable Modem" and the other is the "Reset All Defaults."
The first causes the modem to restart. This is not a big issue since it only takes three minutes, but can be annoying since it may break live streams or active downloads.
Exploiting the second button is a little bit more dangerous, since besides whipping out the modem's settings, it will also renegotiate its status on the ISP's network.
This action can take up to 30 minutes, but Longenecker says that for some ISPs this might also involve calling the provider (like for Time Warner Cable).
Bug can be used in automated attacks
The researcher says that an attacker could craft a malicious link which, when accessed by a user, will automatically trigger the buttons, via a simple CSRF attack.
Placing links like the ones below as the source parameter of an image (src="malicious_link") is all that's needed.
192.168.100.1/reset.htm
http://192.168.100.1/cmConfigData.htm?BUTTON_INPUT1=Reset+All+Defaults
Because browsers don't care what's inside the image HTML tag's source parameter, they will issue a request to those links automatically.
By placing an image tag that has a malicious link as the image source on any Web page, users that view the page will inadvertently reset their ARRIS SURFboard SB6141 modems, sometimes ending up crashing their local Internet connection without knowing why. There's no user interaction needed.
No firmware update available, users at the mercy of ISPs regardless
The researcher discovered the bug at the start of January, and after informing ARRIS, the company failed to issue a new firmware update at the time of writing.
Since the attack is automated and hard to detect, in this case, users have no method of protecting against it. Even if ARRIS would issue a new firmware update, users can't apply it manually, and they'll still be at the mercy of their ISPs.
UPDATE: Following our story, ARRIS reached out with the following statement: "ARRIS recently addressed the reported GUI access issue with a firmware update. We are in the process of working with our Service Provider customers to make this release available to subscribers. There is no risk of access to any user data, and we are unaware of any exploits. As a point of reference, the 135 million number is not an accurate representation of the units impacted. We take product performance very seriously at ARRIS. We work actively with security organizations and our Service Provider customers to quickly resolve any potential vulnerabilities to protect the subscribers who use our devices."

 14 DAY TRIAL //
14 DAY TRIAL //