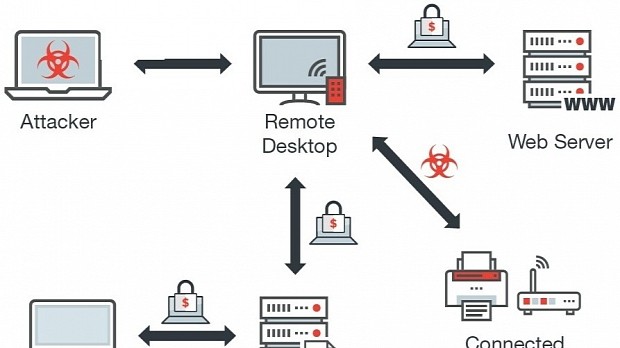
Security researchers say they've discovered a new Crysis ransomware distribution campaign that uses RDP brute-force attacks to compromise the computers of businesses in Australia and New Zealand.
Crooks are scanning the Internet for unsecured, open RDP ports, and are launching brute-force attacks in an attempt to guess the exposed computer's admin password.
If they manage to do it, the crooks install the Crysis ransomware on that specific station, but where possible, they also spread it to other computers on the same network, either by brute-forcing nearby PCs or by leaving Crysis payloads on other network devices, such as printers or routers, which then spread it to other users.
These campaigns have only been seen in Australia and New Zealand, according to Trend Micro researchers.
Crysis wanted to replace TeslaCrypt, but largely failed
The Crysis ransomware, which appeared at the start of 2016, has made a name for itself after it intensified spam levels following the shutdown of the TeslaCrypt ransomware in mid-May.
The crooks behind it made an aggressive move to occupy the void left by TeslaCrypt on the ransomware market, but have somewhat failed, with Cerber, CryptXXX, Locky and Locky's Zepto variants being much more active.
Initially, the group used spam emails that lured users to access a malicious website where they were tricked into downloading malicious files.
The group also used spam with malicious file attachments, a popular method of spreading all kinds of malware, not just ransomware.
Crysis now uses RDP brute-force attacks
In this most recent development, it appears that the Crysis crew is still looking for an identity, now employing brute-force attacks to take hold of and lock devices.
Crysis is not the first ransomware to use RDP brute-force attacks. Other ransomware families use this tactic to more or less success. The list includes ransomware variants such as LowLevel, DMA Locker, Apocalypse, Smrss32, Bucbi or the ransomware distributed by a group called the Julian Assange Corporation.
Because the ransomware uses a strong encryption combo of AES and RSA algorithms, at the time of writing, there is no known way of unlocking files encrypted by Crysis (also known as Virus-Encoder). A good offline backup policy should keep most companies safe, along with a method of recovering locked files.
 14 DAY TRIAL //
14 DAY TRIAL //