The CryptXXX ransomware suffered a mutation during the past week after security researchers from SentinelOne published an exposé about the criminal group behind this threat, revealing that crooks were making around $2,600 each day from their illegal operations.
CryptXXX changes include the usage of new names for the ransom notes (README.html, README.bmp, and README.txt), a new GUI for the portal where users can pay the ransom, and the fact that files encrypted with CryptXXX will no longer feature a custom extension like before.
In hindsight, for an infosec professional, all these changes are easy to explain.
Victims infected with ransomware will normally search for the custom file extension added at the end of each file to detect with what type of ransomware they have they been infected.
Without any custom extension added to the end of encrypted files, users will have a hard time identifying the ransomware's name. Additionally, ransom notes also help in the identification process.
CryptXXX makes identification much harder
For CryptXXX authors, this change was gravely needed since security researchers cracked different CryptXXX versions in the past.
A victim who identifies that they have been infected with CryptXXX may be inclined to wait for a few weeks until security researchers release another CryptXXX decrypter that allows them to recover locked files without paying the ransom.
By making the identification process much harder, CryptXXX authors are introducing a state of confusion and uncertainty in the ransomware identification process that may lead to more ransom payments since users won't be able to pinpoint their infection to a ransomware family that has been deemed "decryptable" so many times in the past.
CryptXXX decrypter doesn't work (at the moment)
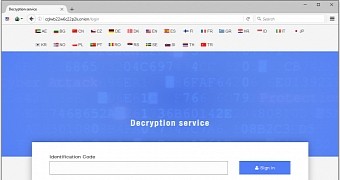
Furthermore, UI changes to CryptXXX's ransom payment site, which is now branded as "Microsoft Decryptor," also prevent visual identification compared to past screenshots for the same ransomware.
In their rush to give CryptXXX a facelift, the crooks have had no time to put out a proper decrypter, the software used by infected users to recover files after they pay the ransom, according to Lawrence Adams of Bleeping Computer.
Furthermore, the live support feature for which CryptXXX was famous, allowing victims to talk to the crooks and get support in paying the ransom and decrypting their files, is now down as well.
Despite a strong distribution campaign, is CryptXXX on its last leg?
After having their ransomware decrypted so many times, TeslaCrypt's coders have simply given up on their operation and moved on to a new ransomware family altogether.
Seeing that CryptXXX is marred by so many encryption problems, don't be surprised if the ransomware just goes away as crooks will likely get tired of constantly fixing bugs and choose to start from scratch.
Nevertheless, right now, they're taking full advantage of their malware, with a rampant campaign called Realstatistics, and by adding password theft capabilities to CryptXXX at the start of June.
CryptXXX devs do it again...release a non-working decryptor. https://t.co/oeuau0nS4r — Lawrence Abrams (@BleepinComputer) July 8, 2016
 14 DAY TRIAL //
14 DAY TRIAL //