The Cyber Threat Alliance, a conglomerate of various cyber-security vendors, has released a report that analyzes and breaks down the recent wave of CryptoWall 3.0 ransomware campaigns.
The Cyber Threat Alliance is made up of security researchers from companies like Symantec, Fortinet, McAfee (Intel Security), Palo Alto Networks, Zscaler, Telefonica, Barracuda, and ReversingLabs, all of which have contributed with their own private information, and pieced together the history and evolution of the CryptoWall ransomware.
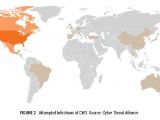
According to the report they've put out, CryptoWall operators have launched 49 different campaigns in the past years, attempting to infect 406,887 users, most of them in North America.
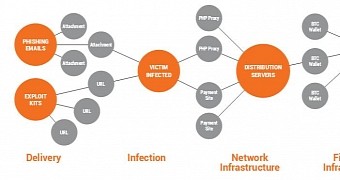
The researchers have also discovered 4,046 different CryptoWall variants, working on an infrastructure that included 839 C&C servers, spread over 5 second-tier IP addresses.
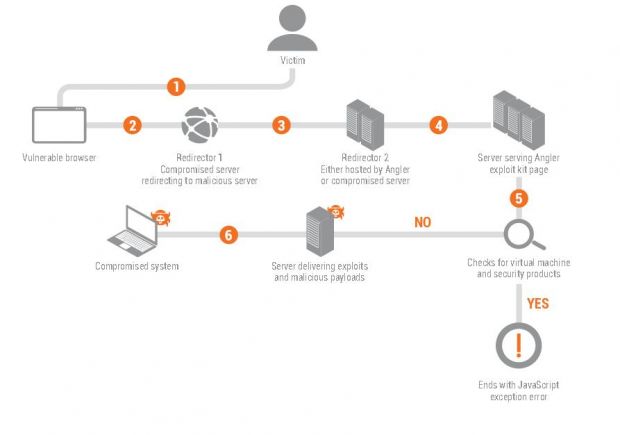
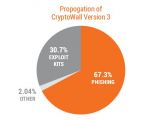
Most of the campaigns leveraged phishing emails (67.3%) and exploit kits (30.7%).
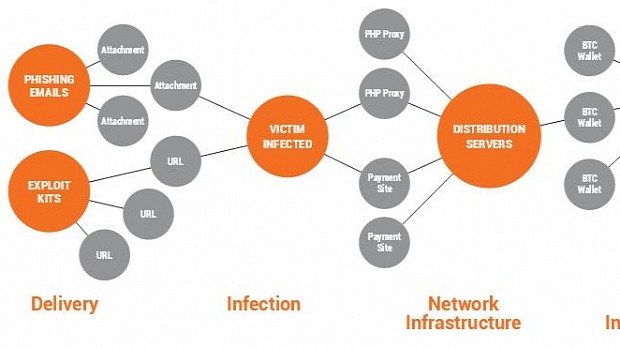
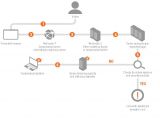
Bitcoin transactions involved in ransoms left a trail that researchers were willing to follow
Because all Bitcoin transactions are logged in the service's blockchain, researchers had the opportunity to take a closer look at the Bitcoin operations that involved the wallet addresses displayed to CryptoWall infected victims.
Mapping out a series of operations that included these publicly displayed wallet addresses and a multitude of intermediary wallets, the Cyber Threat Alliance group has observed that most of them led back to one main Bitcoin account.
It was easy for researchers to conclude that one single cyber-crime was behind all the campaigns. Past transactions and the amount of Bitcoin in the central and lower tier wallets show that the group has made around $325 million / €295 million.
"The first and best way to defend against CryptoWall is to ensure that users are trained in common best practices to avoid the malware infecting their systems," say the researchers, who recommend, besides installing robust antivirus solutions, that companies also deploy more advanced protection measures that use sandboxing techniques.
A few days ago, Kaspersky announced that, together with the Dutch Police, they were releasing all the decryption keys for the CoinVault and Bitcryptor ransomware. These keys will allow ransomware victims to decrypt their files for free. Right now, CryptoWall 3.0 victims don't have this luxury.
 14 DAY TRIAL //
14 DAY TRIAL //