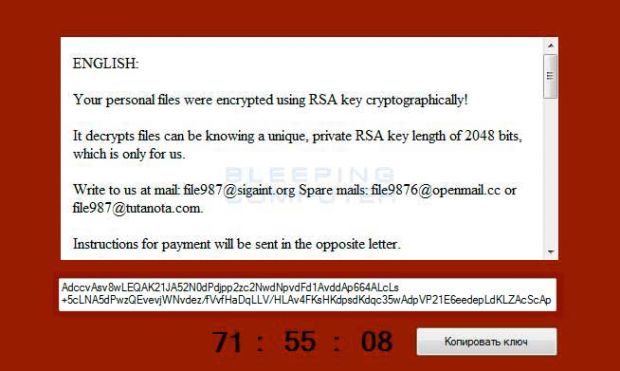
A new ransomware family has been discovered, dubbed CryptoJoker after the .crjoker string that it adds at the end of each encrypted file.
CryptoJoker is relatively new on the malware market, and according to security researchers from MalwareHunterTeam and Bleeping Computer, it is not actively being distributed at this moment.
The ransomware infects users via EXE files disguised as PDF files, so the most obvious infection scenarios would be via spam and spear phishing campaigns.
CryptoJoker's modus operandi is quite similar to what we've seen from all modern ransomware families, infecting computers, encrypting files using AES-256 encryption, and then showing the ransom popup over other active windows.
Victims are encouraged to send an email to three addresses ([email protected], [email protected], or [email protected]) in order to negotiate payment and get their files back.
The ransom note does not list a specific sum of money, so there are chances that the ransomware's author may be convinced to lower their price during negotiations.
Because of the high-end encryption method chosen by CryptoJoker's author, there's no way to decrypt files in the foreseeable future.
Since the ransomware targets 30 file extensions and deletes shadow volume copies, users are left with only two options: recover files from an older archive, or contact the CryptoJoker ransomware author and pay the ransom.
We have contacted Bleeping Computer's Lawrence Abrams requesting information about CryptoJoker's VirusTotal detection rate. As you can see, detection rates are pretty low.
UPDATE: The article was updated to reflect that the CryptoJoker's ransom note is not shown in fullscreen mode, but as a popup over other windows, and that infection occurs via EXE files disguised as PDF files.

 14 DAY TRIAL //
14 DAY TRIAL //