David Chaum, the father of many encryption protocols, has revealed a new anonymity network concept that aims to fix many of Tor's current problems, both in the legal and technical department.
Many scientists have tried to fix TOR in the past with concepts like I2P, HORNET or Vuvuzela. David Chaum's advantage is the fact that the Tor Project actually copied his work in the past, implementing an evolved version of one of his anonymity protocols called Mix Network, also used by Bitcoin's creators.
Mix Network (sometimes called Mixing Network) relies on encrypting data in layers as it passes through intermediary servers. The concept was first published in 1979 and was later used as the basis for the Onion protocol, on which the Tor network was built.
This past Wednesday, on January 6, 2016, Mr. Chaum presented himself at the Real World Cryptography Conference in Stanford, where he revealed a project on which he had worked for the past two years alongside other cryptography experts from four universities in the US, UK, and Holland.
His paper, called "cMix: Anonymization by High-Performance Scalable Mixing," presents an evolution of the Mix Network concept, called cMix, which took into account Tor's advancements, but also addressed some of the issues governments and regular users had with its implementation. The researchers plan to use this new cryptography protocol to build their own, more secure PrivaTegrity network, as an alternative to Tor.
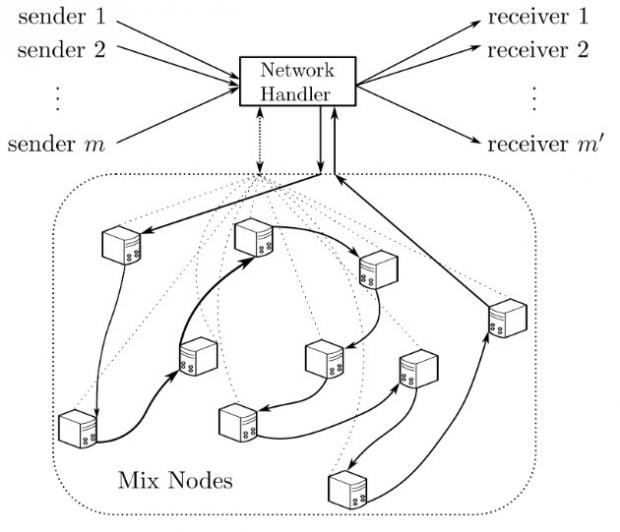
An incredibly simplified explanation of cMix
According to their research paper (page 1 - Section I, and page 4 - Chapter III-D), for each communications path established in a cMix network, the message sender creates connections with a series of trusted servers, with which it shares a series of keys.
When the sender sends out a message, its data is multiplied with all the keys. As the message passes through each server, it is divided with each server's corresponding key, but also multiplied again by a random number. Messages are then stored randomized in each server's buffer.
When the data needs to be retrieved and sent to the receiver, each server will retrieve the message from its random position, divide out the random numbers, and then multiply it with the recipient's keys.
When the data arrives on the recipient's computer, their keys are used to divide the data and decrypt the message.
Better anonymity than on Tor
According to Mr. Chaum, by moving most of the computational operations to the server, instead of the client, cMix achieves the same transfer speeds as Tor, but unlike its predecessor, it is not vulnerable to a series of "tagging" attacks.
Tagging attacks rely on compromising Tor nodes, which on their own allow attackers to tag input slots with their output location. By using cMix's setup, the protocol is not vulnerable to these type of attacks, unless the malicious entity compromises all nodes that participated in the encryption process.
Additionally, researchers said that, in PrivaTegrity, tagging attacks are also blocked by how users set up keys with network nodes.
"PrivaTegrity aims to provide privacy at a technical level that is not penetrable by nation states," the researchers claim. "PrivaTegrity implements a new approach to user identification requiring each user to provide a small but different type of identifying information to each mix node."
But...
This identification may include anything from passphrases to images, from phone numbers to email addresses. "A user reveals comparatively little to any single node, but collectively the nodes possess significant identifying information," researchers revealed.
While its encryption protocol is incredibly strong, the researchers also said that data about users is not 100% anonymous.
In an interview with Wired, Mr. Chaum revealed that, to prevent cybercrime and other nefarious groups from using their network, the researchers behind this initiative are planning to create a PrivaTegrity Council.
This council will provide access to data about users to law enforcement, but only for those who use the network for criminal activities. This council will have nine members from across the world, and all have to agree to release information about users to any government inquiring for data.
With the rising trend of government requesting backdoors to encryption protocols, Chaum and his associates are trying to move the backdoor from the hands of governments to an international council.
While technically as fast as Tor and even more secure from third-party attacks, admitting that a group of nine people get to play judge over your anonymity may deter users from embracing PrivaTegrity.
Currently, Chaum and his team are working on a smartphone IM app to test their PrivaTegrity network.

 14 DAY TRIAL //
14 DAY TRIAL //