Security researchers for ISC (Internet Security Center) have uncovered a new phishing campaign that uses a login form on top of a blurred image of an Office document to trick users into handing over their login details.
This particular phishing campaign is distributed via spam email messages that also contain a blurred-out image, with a link to view the file at the end of the email message.
The link leads back to a Brazilian server, which didn't appear to be hacked, as most phishing hosts regularly are.
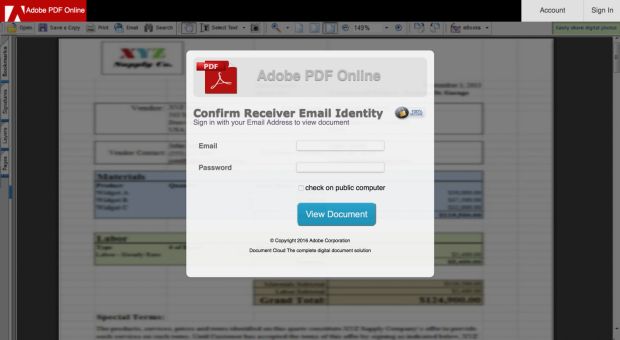
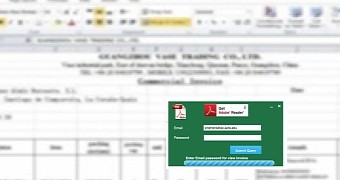
Phishing page login form was very vague
All phishing campaigns have a weakness, and according to ISC researcher Xavier Mertens, this one had several.
For starters, the phishing campaign isn't very well defined. Mertens says that crooks weren't very specific when they crafted the login forms, and victims landing on this page wouldn't have known what login details they should fill in.
"The strange fact is that it is not clear which credentials are targeted: Google, Microsoft or corporate accounts?" Mertens explains. "The success of an efficient phishing is to take the victim by the hand and 'force' him/her to disclose what we are expecting."
Crooks forget phishing kit source code on the server
The researcher also adds that the crooks misconfigured the server hosting this phishing campaign, which allowed him to access all its files, including PHP resources. On the server, Mertens claims he discovered the kit with which the crooks crafted their phishing campaign.
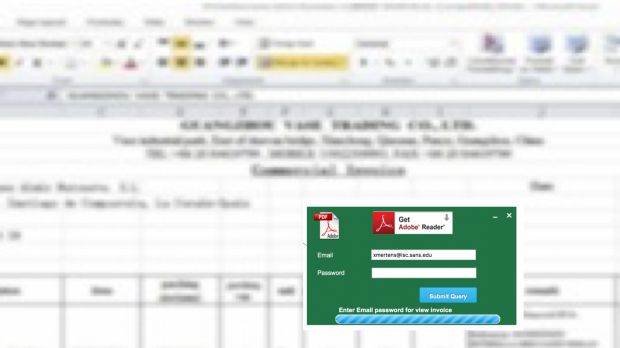
Crooks created the blur effect by taking a low-res image (ex: 300*200px) and displaying it at very high resolutions. On top of this, they came up with a login form that featured JS-based validation of the email address the user entered.
The crooks would check to see if the user entered a valid email address, and showed errors in case the user tried to test the phishing page by entering non-standard data.
Phished data was sent via email to the crooks
Once the JS scripted detected a valid email address, it would send the following details via email to the attacker's email address: email, password, GeoIP details, user-agent string, FQDN computer ID, and the victim's IP address.
The phishing campaign had a second page, one that asked the user to enter their phone number. As with the first step, this detail, if filled in, was sent via email to the crooks.
Mertens says the crooks behind this campaign used two email addresses hosted on Gmail and Inbox.ru to receive their phished credentials.
The lesson here is that if you look long enough at any phishing page, it's quite a piece of cake to find easily detectable flaws, either in the GUI or the page's source code.
 14 DAY TRIAL //
14 DAY TRIAL //