Tech support scammers have come up with a new ingenious scheme to scare victims into calling their fake tech support numbers and pay for services they don't need or are never provided.
This new scheme relies on hijacking a user's normal browsing experience using malicious ads (malvertising) and redirecting him to Web pages where the user is warned about infected files on his computer.
But we've seen this tactic being used many times in the past. The novel element is that the scammers are using IP sniffing software to detect the user's IP, and reverse it back to his ISP's IP pool.
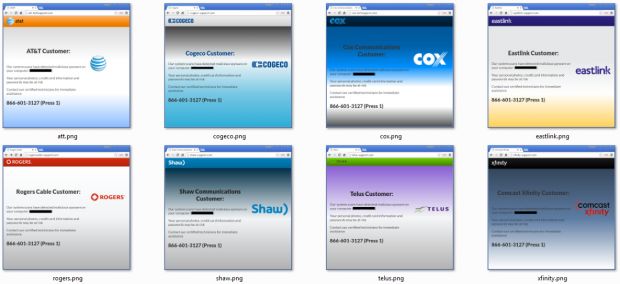
ISP brands used as the scam campaign's central element
Once the scammers know what the user's Internet Service Provider is, the fake tech support page is loaded with branding consistent to his ISP. A message is written across the screen, and even spoken out loud.
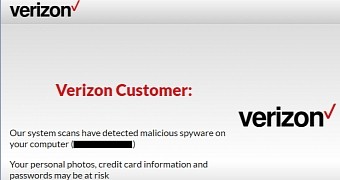
The spoken audio message is in the following format: "[ISP_Name] customer, our system scans have detected malicious spyware on your computer. Your personal photos, credit card information and passwords may be at risk. Contact our certified technicians for immediate assistance."
Below you can listen to one of the messages spoken out loud to users that land on the tech support scams. Audio courtesy of Malwarebytes.
Because the user sees the ISP's branding, he might be convinced the message is authentic and call the tech support number listed on the page, asking for advice on how to disinfect his PC.
Tech support scammers linked to Indian call center
Malwarebytes, the security firm that came across the campaign, called the tech support number and found out it was operating from a call center in India, attached to the support-samurai.com website.
Back in January, a similar tech support scam operating out of India was discovered to be the work of a legitimate Symantec reseller, which the company later disavowed.
This time around, these tech support scammers were using an old trick to convince users to pay for security clean-up services they did not need. The scammers were telling users to open the Windows Run window and type "inf infected files."
"Inf" is a standard Windows CLI command that opens the "C:\Windows\INF" folder. What users didn't know, is that they could have typed anything after "inf" and they would have opened the same folder, such as "inf kanye west is godzilla in disguise".
UPDATE: Something that has escaped our initial report. The ISPs currently targeted by the campaign are: AT&T, Bell Aliant, Bell Canada, BT, Charter, Cogeco, Comcast, Cox, Eastlink, EE, Optimum, Plusnet, Rogers, Shaw, Sky, TalkTalk, Telus, and Time Warner, Verizon.
 14 DAY TRIAL //
14 DAY TRIAL //