Three critical security flaws in BTS stations allow attackers to compromise, hijack, crash mobile cell towers, security researchers from Zimperium have discovered.
BTS (Base Transceiver Station) is the technical term used to describe cellular phone towers we all see every day in our towns, villages, and spread all over the fields, hills, and mountains.
BTS stations are the backbone of every mobile network around the world and are used to relay calls, SMS messages, and data packets from our phones to the mobile operator's data center, which in turn interconnect calls, transmit the SMS messages to their destination, and sends data packets over the Internet to the servers we are trying to reach.
BTS stations are universally deployed, regardless if the underlying mobile network runs on GSM, UTMS, or LTE technologies.
Flaws affect multiple products from multiple vendors
Mobile security firm Zimperium, the company that found the Stagefright bug, says it discovered three critical flaws in several software packages that run on BTS stations.
According to Zimperium, other software packages not included in their tests might also be affected since they all seem to run in the same manner, with a similar architecture.
Affected vendors and their software include Legba Incorporated (YateBTS <= 5.0.0), Range Networks (OpenBTS <= 4.0.0 and OpenBTS-UMTS <= 1.0.0), and OsmoCOM (Osmo-TRX <= 0.1.10 and Osmo-BTS <= 0.1.10).
There are currently three issues which mobile operators and BTS software vendors need to address in their equipment.
Issues allow attackers to take over BTS stations
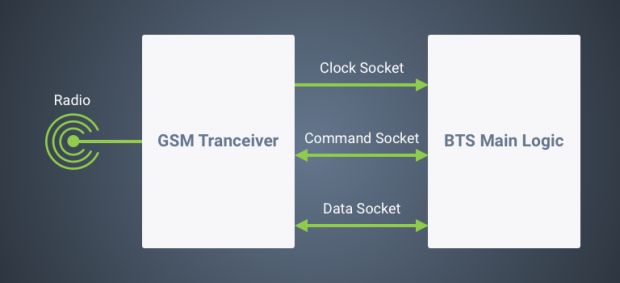
The first is a bug in a core BTS software service that exposes the device to external connections, allowing an attacker to reach the BTS station's transceiver via the Internet.
Attackers can send UDP packets to certain management ports (5700, 5701, 5701) and take advantage of the device's built-in features. This allows the attacker to take remote control of the BTS station, alter GSM traffic, extract information from the passing data, crash the BTS station, or worse.
In this case, Zimperium recommends that companies bind the sockets used for control and data exchange only to the local interface (127.0.0.1), or deploy a firewall to block external traffic.
The second issue is a memory buffer overflow caused by oversized UDP packets. This is a classic remote code execution flaw (RCE) that lets the attacker run malicious code on the device. This bug is as dangerous as the attacker's skills.
The third issue relates to the first. If the attacker can send custom UDB traffic to the BTS station, because the control channel features no authentication, an attacker can execute commands on the BTS station's transceiver module. The transceiver is the main hardware component in the BTS station rig, which sends and receives data between the radio antenna and the BTS core software.
This particular flaw allows an attacker to control the transceiver module remotely without having to enter any administrative credentials.
Zimperium says the attacker with access to the control channel can turn the BTS off, jam antenna radio frequencies, or change the BTS identity, removing the BTS from the mobile operator's network or making it behave like another BTS station from the same network, and carry MitM attacks.
All affected vendors have pushed patches, but Range Networks has reverted fixes for the first two issues in OpenBTS on July 6 and July 13, reintroducing the vulnerabilities in its software after it previously fixed them on May 6.
 14 DAY TRIAL //
14 DAY TRIAL //