Security researchers from Arbor Networks have cracked the Doman Generation Algorithm (DGA) used by the Sphinx banking trojan, which, in theory, would allow security firms and authorities to intervene and take down the botnet.
The Sphinx trojan appeared in late August 2015 and is another banking trojan put together using the leaked source code of the infamous Zeus banking trojan.
Just like the original Zeus and subsequently created banking trojans, Sphinx infects victims and connects to an online server to retrieve instructions and further modules.
By default, the trojan includes a list of IP addresses and domains in its source code to which Sphinx connects. These are its primary command and control (C&C) servers.
Sphinx added a DGA-based backup C&C system
In recent Sphinx versions, besides this static C&C server details, the trojan's authors added support for a backup C&C server infrastructure, in case authorities take down the default C&C system.
According to Arbor's Dennis Schwarz, this backup C&C server system is based on a DGA, an algorithm that generates random domain names, of only which the malware's author knows and registers in advance to host the trojan's backend in case of emergency.
Using DGAs is a common practice among all sorts of malware, not just banking trojans, some of them using DGAs as the primary C&C server system.
Arbor cracks Sphinx backup C&C DGA
The good news, according to Schwarz, is that this DGA algorithm is quite simplistic and the Arbor team cracked it.
The researcher says the DGA uses the current date as the seed algorithm from which it generates random strings of 16 characters and appends the ".com" domain at the end. The DGA generates 128 domains per day and new domains every day.
Cracking this algorithm allows security researchers to know all the possible locations where the botnet might be hosting its C&C server for the foreseeable future.
Knowing the location of both static and backup C&C servers would, in theory, allow authorities to step in and take down the botnet's command and control infrastructure.
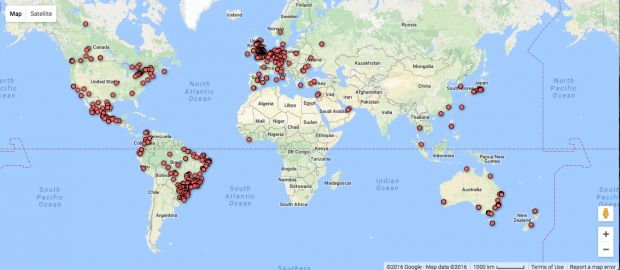
Sphinx botnet has only 1,230 bots
For its part, Arbor has open-sourced the code that calculates the backup domains. The company has also sink-holed a couple of C&C domains on October 13, to get an understanding of the botnet's size.
According to their findings, the botnet only had 1,230 bots on that particular day, which is an incredibly small number when compared to other banking trojan botnets that have tens of thousands, and even millions of bots.
Arbor says that most of these bots are located in Brazil, which is in line with an IBM report from August that saw a rise of Sphinx infections targeting Brazilian financial institutions.
Previously, Arbor Networks researchers had cracked the DGA of the Mad Max botnet, allowing them to accurately guess all the C&C domain names the malware would have used in the upcoming months and years.

 14 DAY TRIAL //
14 DAY TRIAL //