Researchers from Cisco's OpenDNS security team have uncovered a complex phishing scheme aimed at collecting user credentials from various Bitcoin-related services, which, under a closer scrutiny, led back to a known bulletproof hosting firm.
The first to stumble over this campaign were the security researchers from CYREN, who spotted it in the first week of June.
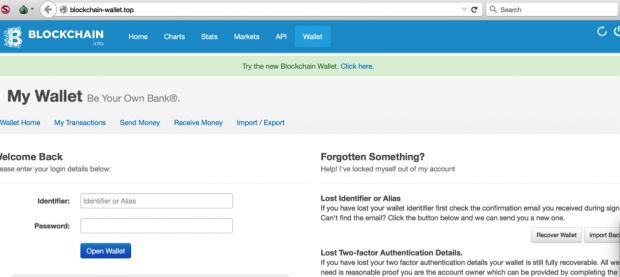
The crooks behind the phishing campaign were relying on pixel-perfect cloned Web pages for various Bitcoin wallet services, with a special focus on Blockchain.info, one of the most important sites in the Bitcoin ecosystems.
AdWords campaigns drove traffic towards the phishing pages
Phishers were leveraging a Google AdWords campaign to lure victims into accessing their malicious sites, registered using typosquatting domains, such as bioklchain.info instead of blockhain.info.
What caught the eye of the OpenDNS team was that some of these websites were hosted on IP addresses that had a history.
Leveraging OpenDNS' huge Whois database, the team discovered that the same IP had hosted a slew of malicious sites in the past, such as pharma spam and other phishing domains, for services such as banking portals, iCloud accounts, and more.
Furthermore, most of these phishing domains were registered under only six email addresses. OpenDNS says the oldest domain of these domains was registered on May 26, 2016.
Malicious phishing pages hosted on a bulletproof hosting provider
The IP belonged to a hosting company called Novogara registered in the Seychelles. The firm's previous name was QUASINETWORKS. Prior to that, it was named Ecatel and initially operated in the Netherlands until December 2015.
In the Web hosting biz, Novogara is what's called a "bulletproof hosting provider," referring to companies that go out of their way to protect their customers. This can be useful for users seeking anonymity and privacy against oppressive governments, but can also be abused by cyber-criminals.
In the past, Novogara was linked to sites hosting child pornography, spam, or from where DDoS traffic originated. The company's toxic traffic got so bad that, in 2008, fellow companies stopped peering with Novogara (Ecatel back then). In 2012, the Anonymous hacker collective executed multiple DDoS attacks against the network because it was hosting child pornography.
In an email statement, a Novogara representative told Softpedia that "illegal activities are always dealt with by our abuse department."
Nevertheless, if it's not Novogara, then it's somebody else. These types of companies exist everywhere, from the US to Romania, and from Russia to China, and while they use offshore jurisdictions to protect clients from censorship, but they are also indirectly involved by cyber-criminal groups in their campaigns, groups who value their services.
UPDATE: Added statements from Novogara spokesperson. Updated title to reflect the fact that Novogara was not willingly part of the campaign.

 14 DAY TRIAL //
14 DAY TRIAL //