Google Project Zero security researcher Tavis Ormandy has discovered that one of Comodo's tech support tools packed with many of the company's security products leaves the door open for attackers to a with admin privileges on the user's PC.
Ormandy noticed users complaining online about a VNC server that started on their Windows systems where they installed Comodo Antivirus, Comodo Firewall, or Comodo Internet Security.
Comodo tech support tool at the core of the problem
The researcher investigated the issue further and discovered that to blame for this problem was a remote desktop tool called GeekBuddy, which Comodo was bundling with its security software.
GeekBuddy was used by its tech support staff to debug problematic computers from afar. The application allowed Comodo staff to connect from remote locations by opening a VNC server on the user's PC.
If the user was connected to the Internet, anyone could access the user's computer using this backdoor. If the computer was offline, anyone could do the same from a local network.
GeekBuddy versions had no password, or used a weak one
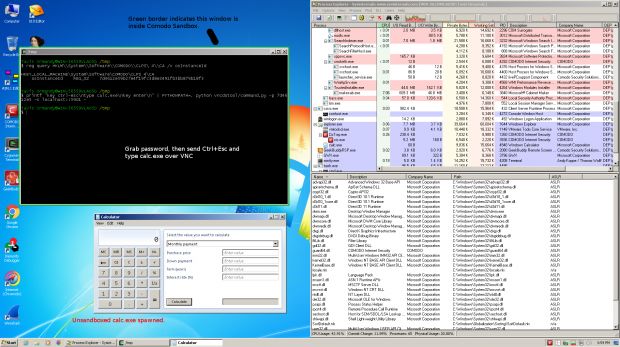
In GeekBuddy's first iterations, the tool didn't even include a password, meaning anyone could just connect to the victim's PC using an IP:port combination.
Users complained about this problem, and in later GeekBuddy versions, Comodo introduced a password. The Google researcher says that this password is easy to guess, being composed of data stored in each computer's Windows Registry.
"The password is simply the first 8 characters of SHA1 (Disk.Caption+Disk.Signature+Disk.SerialNumber+Disk.TotalTracks)," Ormandy revealed.
Since Comodo installed GeekBuddy with full admin privileges, any attacker connecting through Comodo's support tool would have had full control over the system.
To prove his point, Ormandy provided a simple three-line exploit that discovered a workstation's SHA1 string, cut the first eight digits, and supplied them to the attacker.
The researcher informed Comodo of the issue on January 19, and subsequently released GeekBuddy 4.25.380415.167 to address the reported issues.
Mr. Ormandy had previously probed Comodo's software when it discovered that the antivirus maker was also shipping an insecure version of the Chromium browser, dubbed internally Chromodo. Mr. Ormandy is famous for discovering security issues in many high-profile security companies like Avast, AVG, Malwarebytes, Trend Micro, FireEye, and many others.
UPDATE: Comodo has come out to clarify that only its support staff can connect to GeekBuddy, through special company relay servers, meaning remote attackers could not employ this flaw. On the other hand, malware that is already present on the system could use it to escalate its privileges and gain more intrusive capabilities.
No response from Comodo yet. Let's hope they're not just going to leave everyone vulnerable until the 90day clock runs out. #wtf #antivirus — Tavis Ormandy (@taviso) January 26, 2016
Well, Comodo wins as the most braindead and shady software I've seen so far. If you work for Comodo, please contact me. — Tavis Ormandy (@taviso) January 22, 2016
Comodo Internet Security installs a VNC server with predictable password by default. https://t.co/HQXVeKgMLT ¯\_(ツ)_/¯ — Tavis Ormandy (@taviso) February 18, 2016

 14 DAY TRIAL //
14 DAY TRIAL //