Cisco's Talos security group has released a free tool that can scan networks for routers infected with the SYNful Knock malware.
To run SYNful Knock Scanner, developers need Python 2.7 or higher, along with the scapy Python library, version 2.3.1 and higher.
SYNFul Knock, the malware, works by loading specific modules in the router's memory that can execute a series of malicious operations.
These modules are loaded when attackers send specially-crafted TCP packets with altered SYN flags.
Cisco designed its scanner around this modus operandi. The SYNful Knock Scanner works by letting network administrators send malicious packets themselves, and then watch the response of routers on a network.
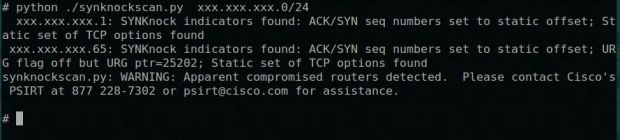
If irregular activity is detected, a message like the one embedded in the image below is shown.
In its initial report, security vendor FireEye said that Cisco router models Cisco 1841, Cisco 2811 and Cisco 3825 were affected. The company did not rule out the possibility that other routers may also be vulnerable.
This free tool is available on Cisco's website and needs to be run with root privileges.
Cisco experts also warn that the tool does not detect impacted routers on networks that run NAT. To avoid this issue, they recommend that the SYNful Knock Scanner be run from a location which does not have NAT between it and the scanned equipment.

 14 DAY TRIAL //
14 DAY TRIAL //