Cisco has released two security advisories today, both addressing exploits recently dumped online by The Shadow Brokers, a group/individual selling hacking tools stolen from the Equation Group, a cyber-espionage organization believed to have ties with the US National Security Agency (NSA).
Hacking tools from The Shadow Brokers leak named EPICBANANA, JETPLOW, and EXTRABACON, contain exploits that can compromise Cisco devices.
These affect Cisco firewall products such as devices from the ASA line, PIX firewalls, and Cisco Firewall Services Modules (FWSM).
Cisco fixes zero-day leaked by Shadow Brokers
According to Cisco, these hacking tools contain exploits that leverage two vulnerabilities, one that Cisco knew about, and one they didn't.
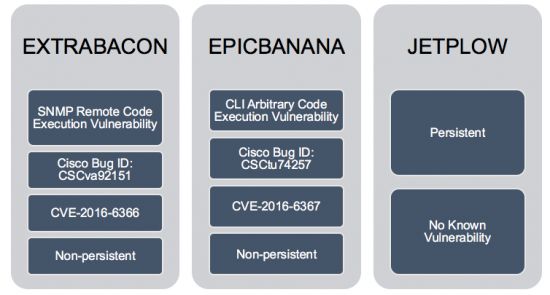
The zero-day vulnerability is CVE-2016-6366. According to Cisco, this is a vulnerability in the Simple Network Management Protocol (SNMP) code of Cisco Adaptive Security Appliance (ASA) software.
The vulnerability can allow an unauthenticated, remote attacker to cause a reboot of affected products, which leads to remote code execution (RCE). RCE flaws are some of the most dangerous security flaws because they enable a skilled attacker to take over the device.
Cisco reminds companies to upgrade their products
Besides the zero-day, Cisco said they found code that tried to exploit an older Cisco vulnerability, CVE-2016-6367, which the company fixed in 2011.
This is a vulnerability in the command-line interface (CLI) parser of Cisco Adaptive Security Appliance (ASA) Software that could allow an authenticated, local attacker to create a denial of service (DoS) condition or potentially execute arbitrary code on the affected device.
The company has now reissued this alert to remind businesses around the world to upgrade the firmware on their devices.
Cisco handled the entire situation very professionally
Cisco responded very well to the Shadow Brokers leak, which was dumped online on August 13 but made news headlines around the world on Monday, August 15.
The company's engineers sifted through all the data dumped online by the hackers, isolated the exploits affected its devices, and analyzed their features.
According to Cisco's Omar Santos, CVE-2016-6366 was found in the Equation Group's EXTRABACON utility while CVE-2016-6367 was included inside EPICBANANA and JETPLOW. Santos claims JETPLOW is an enhanced version of EPICBANANA, with better persistence capabilities.
Fortinet, another firewall equipment vendor for which The Shadow Brokers leaked exploits, also said it patched the vulnerabilities included in the EGREGIOUSBLUNDER exploit and recommended customers to upgrade to FortiGuard versions 5.x.
Other exploits targeted the firewalls of Chinese vendor TOPSEC, who remained quiet, but Chinese hardware vendors rarely put out security advisories.
UPDATE [August 19, 2016]: WatchGuard addressed the issue of the ESCALATEPLOWMAN exploit, which targeted RapidStream devices, a company which WatchGuard acquired in 2002. These products were discontinued, and the exploit did not affect WatchGuard native products, the company said.

 14 DAY TRIAL //
14 DAY TRIAL //