Cisco has published a tell-all blog post today in which the company reveals how French software maker Tuto4PC (also known as Eorezo Group and Wizzlabs) has been pushing unwanted programs behind the users' backs, some of which exhibit malware-like behavior.
Cisco's Talos security team started the investigation by taking a look at some "generic" trojan detections they could not explain.
Searching through mountains of telemetry data, the networking and security vendor discovered that this generic trojan, which they later dubbed Wizz, was actually part of software built and distributed by Tuto4PC.
Tuto4PC software behaves "exactly" like malware
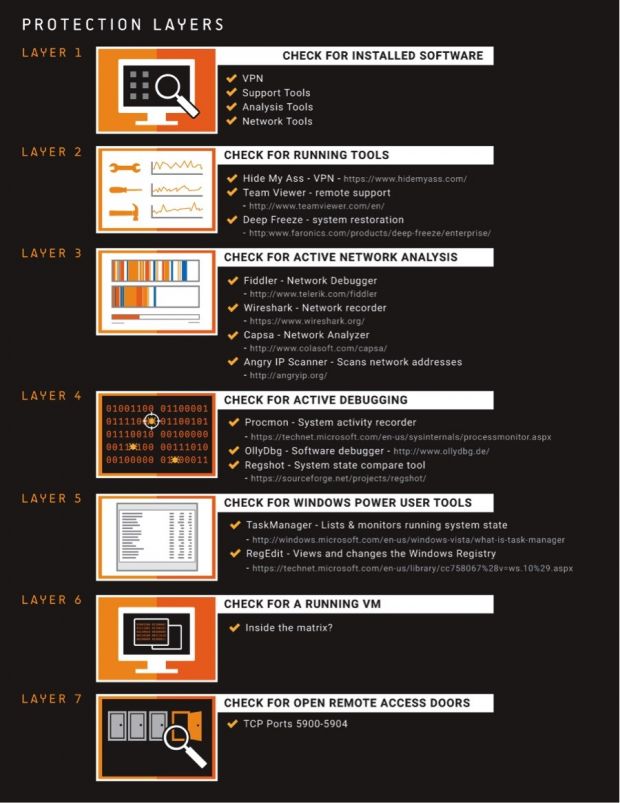
After installation, this software would go through a series of checks, identical to ones seen in today's malware. Tuto4PC's software would check for the presence of sandboxes, antivirus software, security forensics tools, remote desktop sessions, and installed browsers.
It would then collect all this data and send it to its server via an encrypted channel, exactly how infostealers gather reconnaissance information for today's spyware families or banking trojans.
"The funny thing here is that whilst spending so much time on anti-sandbox, anti-analysis techniques the authors did not appear to devote the same time and effort into encryption, simply copy and pasting from an MSDN blog," Cisco researchers noted, revealing that the encryption key was actually available online in an encryption how-to article on Microsoft's site.
Tuto4PC was pushing unwanted software to users' computers
With access to the software's communications channel, researchers were quick to discover that the Tuto4PC software was installing other software packages behind the user's back.
Because the Tuto4PC software gained admin privileges during its setup, it was then able to run silent installations of other software. This happened with no user prompts, not showing anything on the user's screen, or prompting him to agree to a license agreement.
A closer look at the software reveals that the malicious module in the original Tuto4PC software (the Wizz trojan) also had backdoor capabilities. These features allowed Tuto4PC to run any code they wanted, or install any other piece of software, and even actual malware, on the user's computer.
The company has a history of PUP accusations
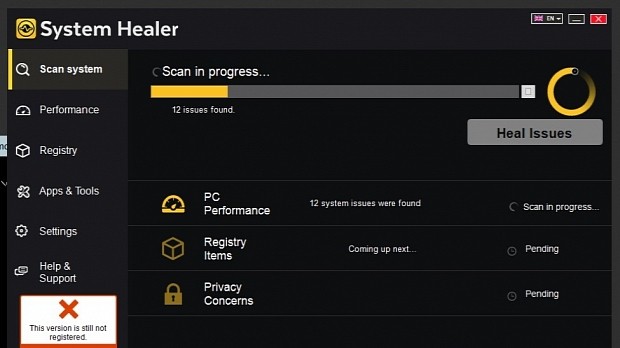
Cisco says that they've seen this malicious behavior in a couple of the company's software packages, naming the OneSoftPerDay and System Healer utilities.
Based on statistics from Tuto4PC's website, Cisco says that 12 million users that installed the company's various widgets and utilities may have a backdoor running on their PC, with Tuto4PC in command of what reaches their computer.
Researchers found 55 domains through which Tuto4PC software was distributed to users. Additionally, Cisco's team also unearthed evidence of the company's past wrongdoings.
Articles in the French media reveal that in the last four years, Tuto4PC has been warned by French regulators to stop installing software without prior approval from computer owners, but the company has managed to drag on proceedings and escape without a fine or a more severe penalty until now.
 14 DAY TRIAL //
14 DAY TRIAL //